
10 Steps to Configure Magento 2 Security Suite Module
Tired of installing and updating several security extensions to keep your store safe? Magento 2 Security Suites offer a safety solution for Magento. Every day, hackers target millions of unprotected Magento 2 stores. The module prevents attacks from compromising customer data and harming the business's reputation.
This tutorial explains the Magento 2 security suite setup and configuration.
Key Takeaways
-
Security Suite adds reCaptcha to block spam and bots.
-
Admin action logs track all backend system changes.
-
Two-factor authentication prevents unauthorized admin access attempts.
-
Advanced permissions control what each admin can access.
-
GeoIP tracking looks for login attempts from unusual locations.
-
Automated features maintain database performance and security logs.
How Does a Magento 2 Security Suite Work?
“A Magento 2 Security Suite protects stores from various threats.”
Security Suite adds Google Invisible reCaptcha to block spam and bots. The system tracks all admin actions on the back end. You can view each logged action with complete details. The suite sends alerts about suspicious login attempts.
Two-factor authentication adds an extra security layer. Admins must enter a code from Google Authenticator.
The suite offers IP whitelisting for trusted networks. Advanced permissions control what each admin can access. You can restrict access to products and categories. The suite includes GeoIP tracking for login locations.
Auto-cleaning features prevent database overload from logs. The system can restore previous settings when needed.
Fundamental Functionality of a Magento 2 Security Suite
1. Google Invisible reCaptcha Integration
-
Form protection adds security to customer-facing forms with minimal disruption to user experience.
-
Custom form support extends protection to any form through url and selector configuration.
-
The guest-only mode applies captcha verification to non-logged-in visitors.
-
IP whitelisting exempts trusted network addresses from captcha verification requirements.
-
Several position options allow the placement of captcha badges in various screen locations.
2. Admin Actions Logging
-
Complete activity tracking records all administrator actions in the backend system.
-
Change restoration allows reverting unwanted modifications with a single click.
-
Session monitoring displays all active admin sessions with termination capabilities.
-
Page visit history maintains records of admin navigation throughout the system.
-
GeoIP integration shows the geographic origin of each login attempt.
3. Two-Factor Authentication
-
Google Authenticator integration requires a time-based code alongside passwords.
-
QR code setup allows quick configuration on mobile authentication apps.
-
IP exemptions allow trusted networks to bypass the two-factor rule.
-
Time drift management keeps code verification working despite device time differences.
-
Per-user configuration applies two-factor requirements to administrator accounts.
4. Advanced Permissions Management
-
Granular access control restricts administrators from accessing store sections.
-
Product-level restrictions limit which catalog items users can adjust.
-
Category management controls which product categories each user can access.
-
Store view limitations confine administrators to store views or websites.
-
Order processing restrictions control access to orders, invoices, and shipments.
5. Automated Security Maintenance
-
Log auto-cleaning prevents database bloat by removing old security records.
-
Email notifications alert security teams about suspicious login activities.
-
Login attempt monitoring tracks successful, failed, and suspicious access attempts.
-
Cron task integration schedules security maintenance during low-traffic periods.
-
Database updates maintain current GeoIP information for location tracking.
Steps to Configure the Magento 2 Security Suite Extension
Step 1: Access Configuration Settings
-
Navigate to Stores > Configuration > Extensions
-
Locate the Security Suite section in the menu
Step 2: Configure Google Invisible reCaptcha
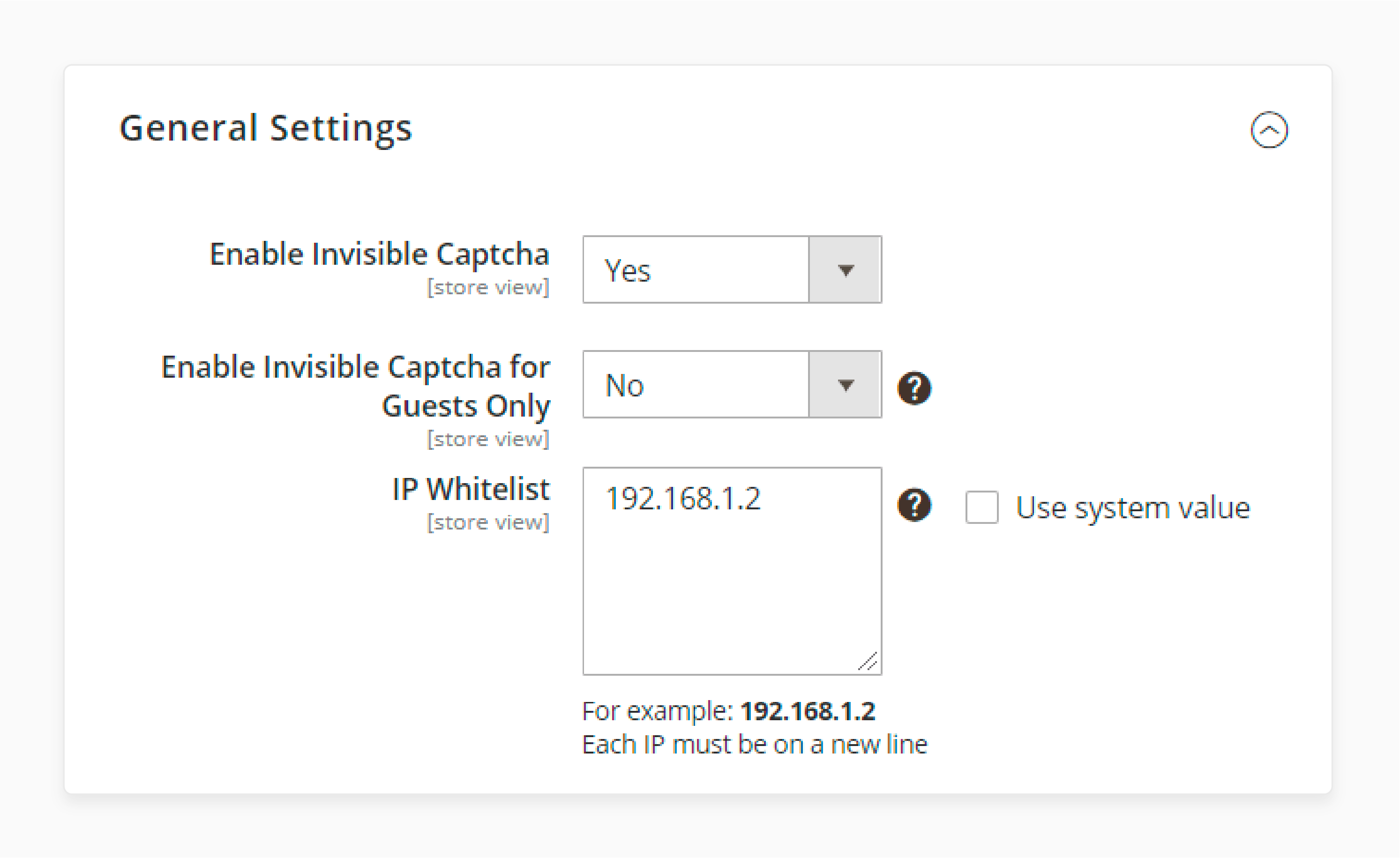
-
Expand the General Settings section
-
Set Enable invisible captcha to "Yes"
-
Generate Site key and Secret key from Google:
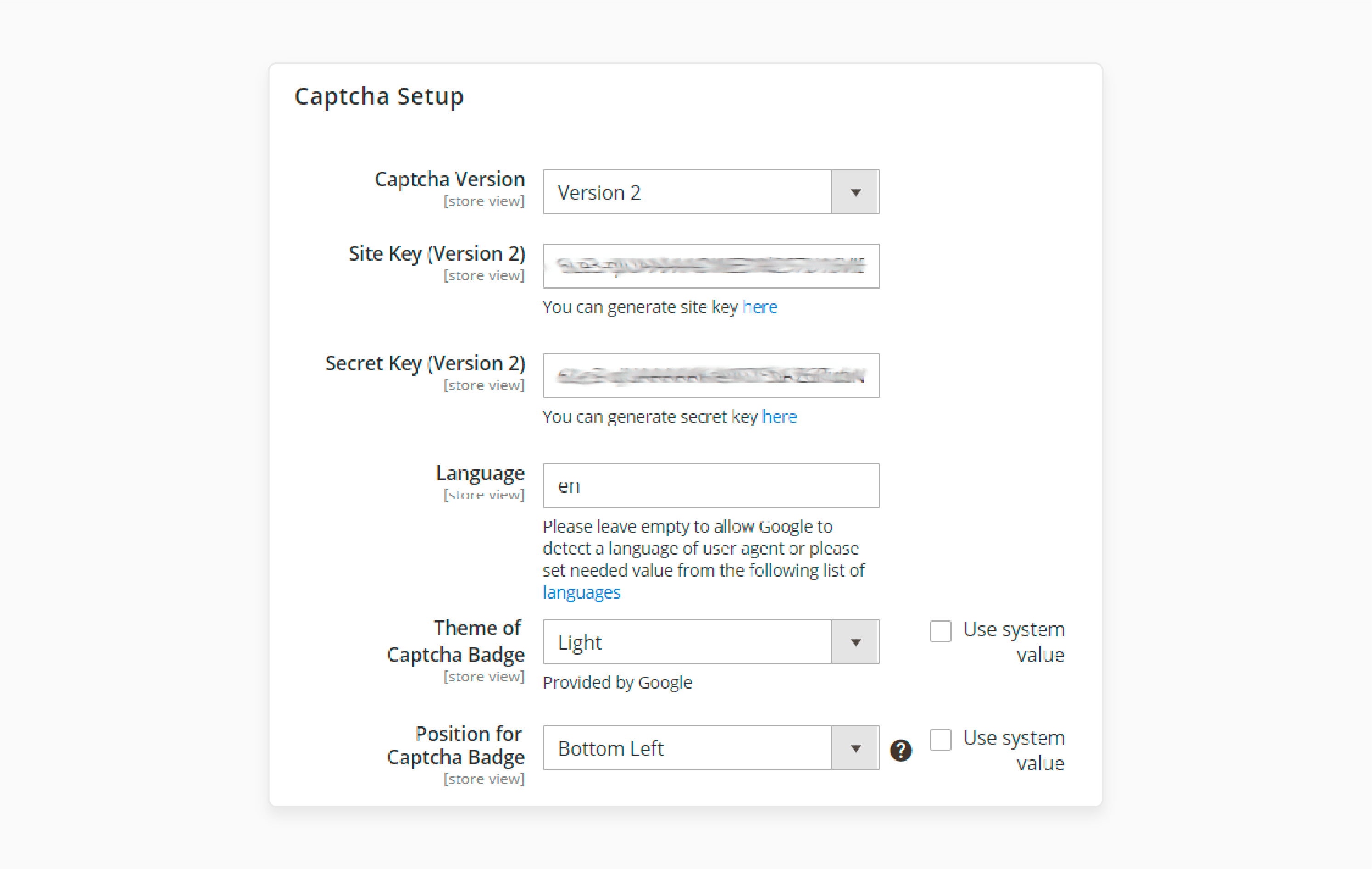
-
Click the provided link to access Google reCAPTCHA
-
Set a name for your reCAPTCHA
-
Select the "Invisible reCAPTCHA badge" option
-
Enter your domain
-
Accept Terms of service
-
Click Submit
-
-
Copy the generated Site key and Secret key to the respective fields
-
Select Language (leave empty to auto-detect)
-
Choose the Theme of the Captcha Badge
-
Select Position for Captcha Badge (Bottom Right recommended)
Step 3: Add reCaptcha to Forms
-
Go to the Advanced Settings section
-
Add URLs for reCaptcha in the "Urls to enable" field:
-
Default URLs include: customer/account/createpost, newsletter/subscriber/new, review/product/post, contact/index/post
-
Add custom URLs on separate lines
-
-
Add CSS selectors in the "Selectors for forms" field:
-
Default selectors include forms for account creation, newsletter, reviews, and contact
-
Add custom selectors on separate lines
-
-
Set "Enable Invisible Captcha for guests only" if needed
-
Add trusted IP addresses to the whitelist (one per line)
Step 4: Configure Admin Actions Log
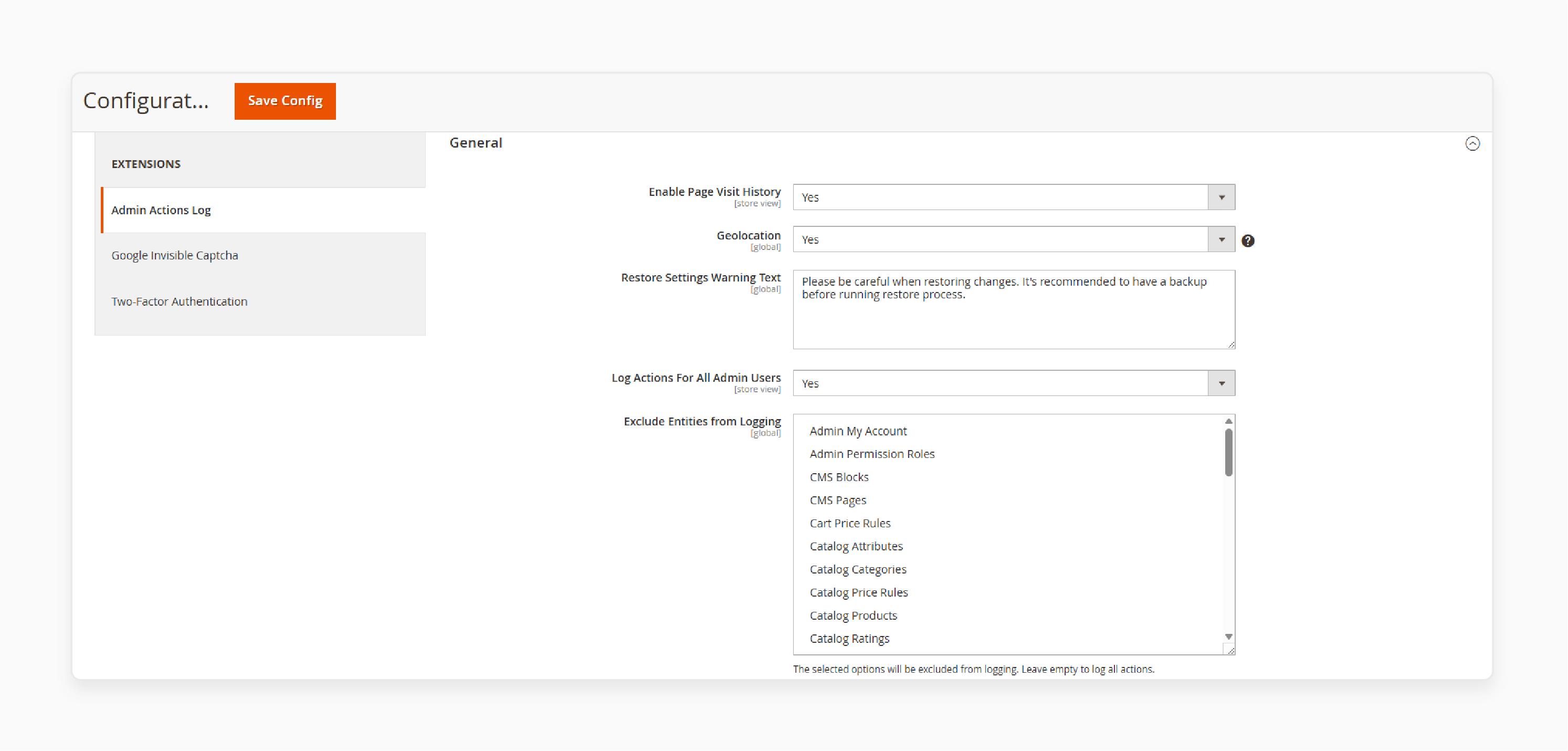
-
Navigate to the Admin Actions Log section
-
Set Enable Page Visit History to "Yes" to track admin page visits
-
Set Use GeoIP to "Yes" to track admin login locations
-
Add Restore Settings Warning Text for the restore feature
-
Choose whether to log actions for all admin users or specific ones
Step 5: Set Up GeoIP Database
-
Go to the GeoIP Data section
-
Click Download and Import to get the latest database
-
Import your own data files using the Import option if preferred
Step 6: Configure Log Auto-Cleaning
-
Expand the Log Auto-Cleaning section
-
Set days for Actions Log Auto-Cleaning
-
Set days for Login Attempts Auto-Cleaning
-
Set days for Visit History Log Auto-Cleaning
Step 7: Set Up Email Notifications
-
Configure Email Notifications for login attempts:
-
Turn on notifications for successful logins
-
Turn on notifications for unsuccessful logins
-
Set the number of unsuccessful login attempts
-
Turn on notifications for suspicious logins
-
-
Select Email Sender for each notification type
-
Choose Email Templates
-
Add recipient email addresses
-
Define suspicious login criteria:
-
From New Device
-
With New IP Address
-
From New Location
-
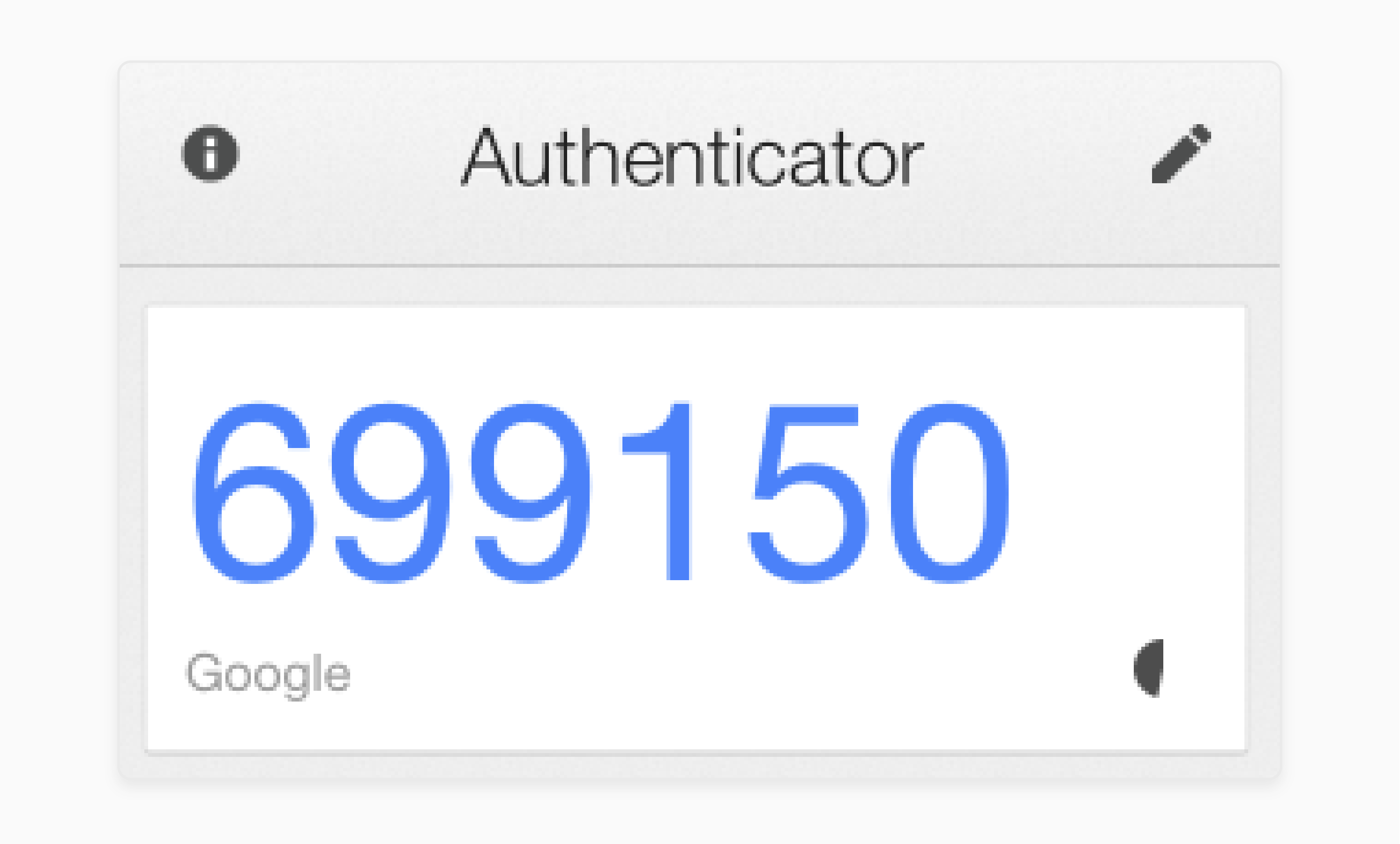
Step 8: Configure Two-Factor Authentication
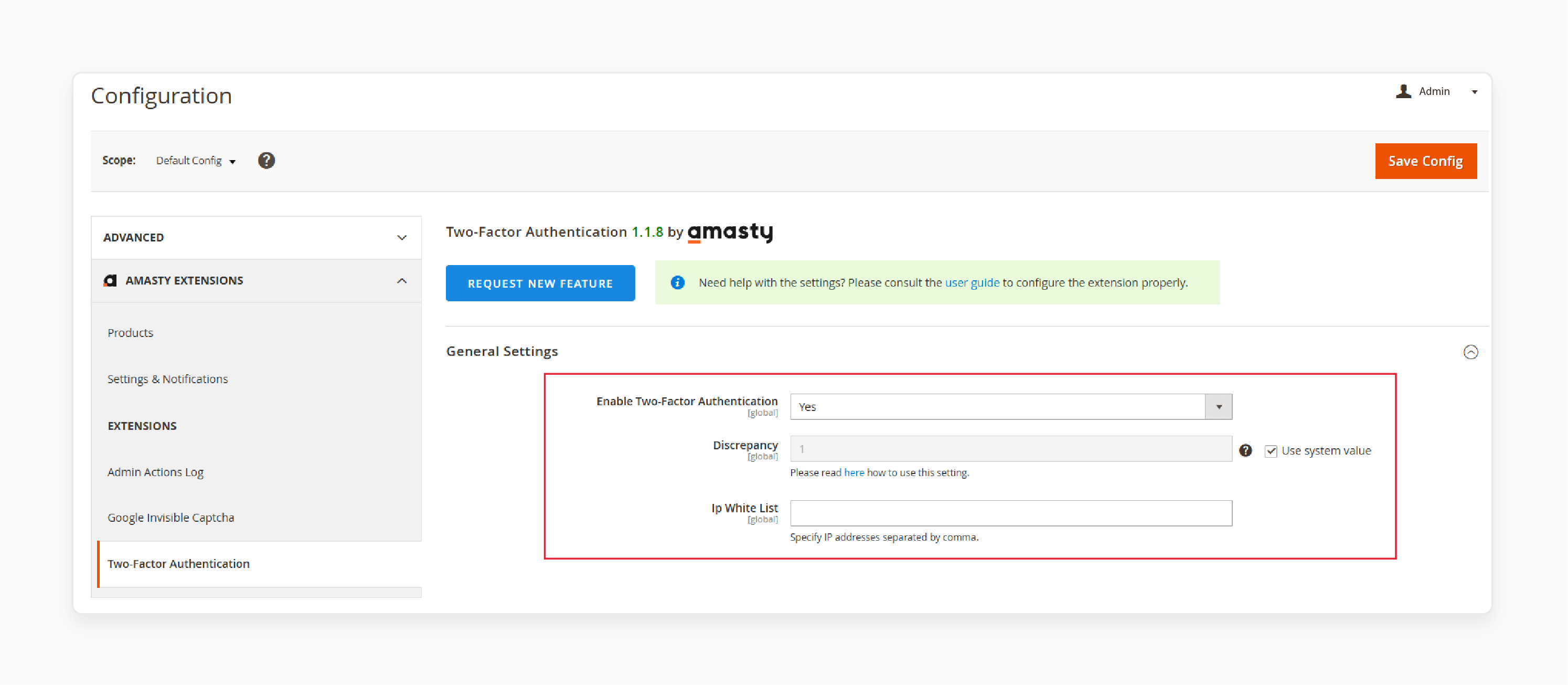
-
Open the Two-Factor Authentication tab
-
Set Enable Two-Factor Authentication to "Yes"
-
Adjust Discrepancy value for time drift in verification codes
-
Add trusted IP addresses to the IP White List
Step 9: Set Up Advanced Permissions
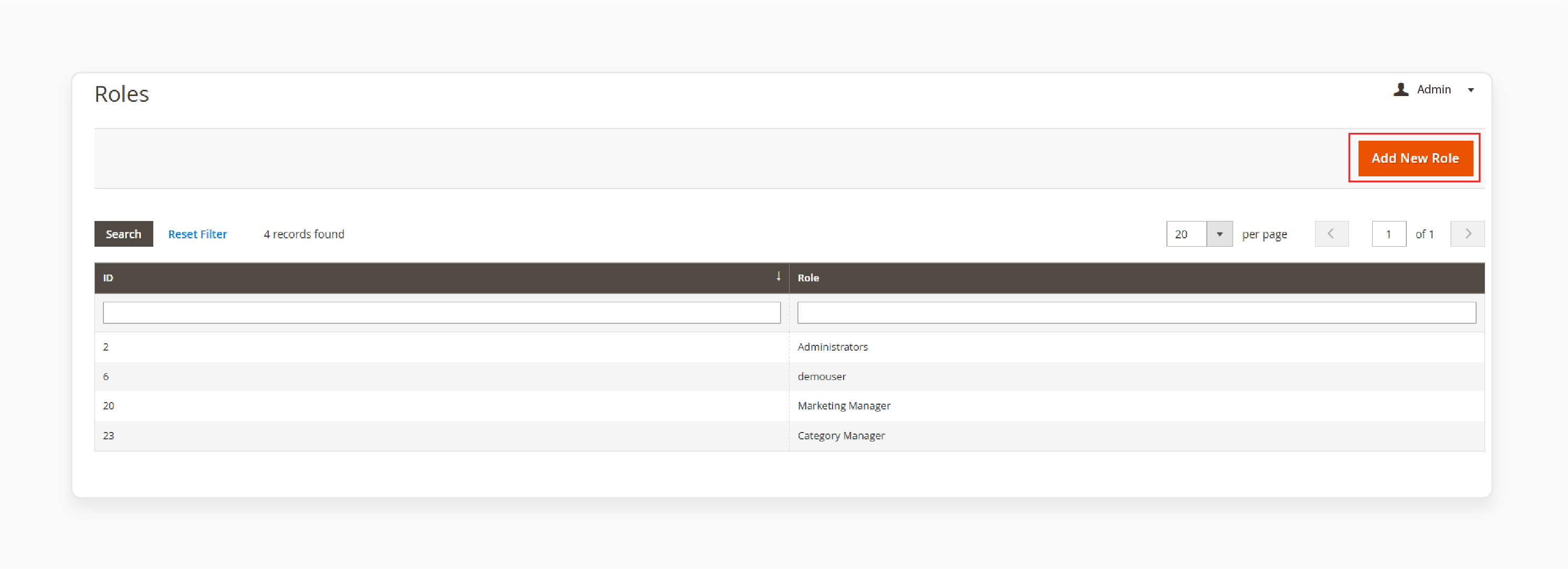
-
Go to System > Permissions > User Roles
-
Create or edit a role
-
Configure access restrictions:
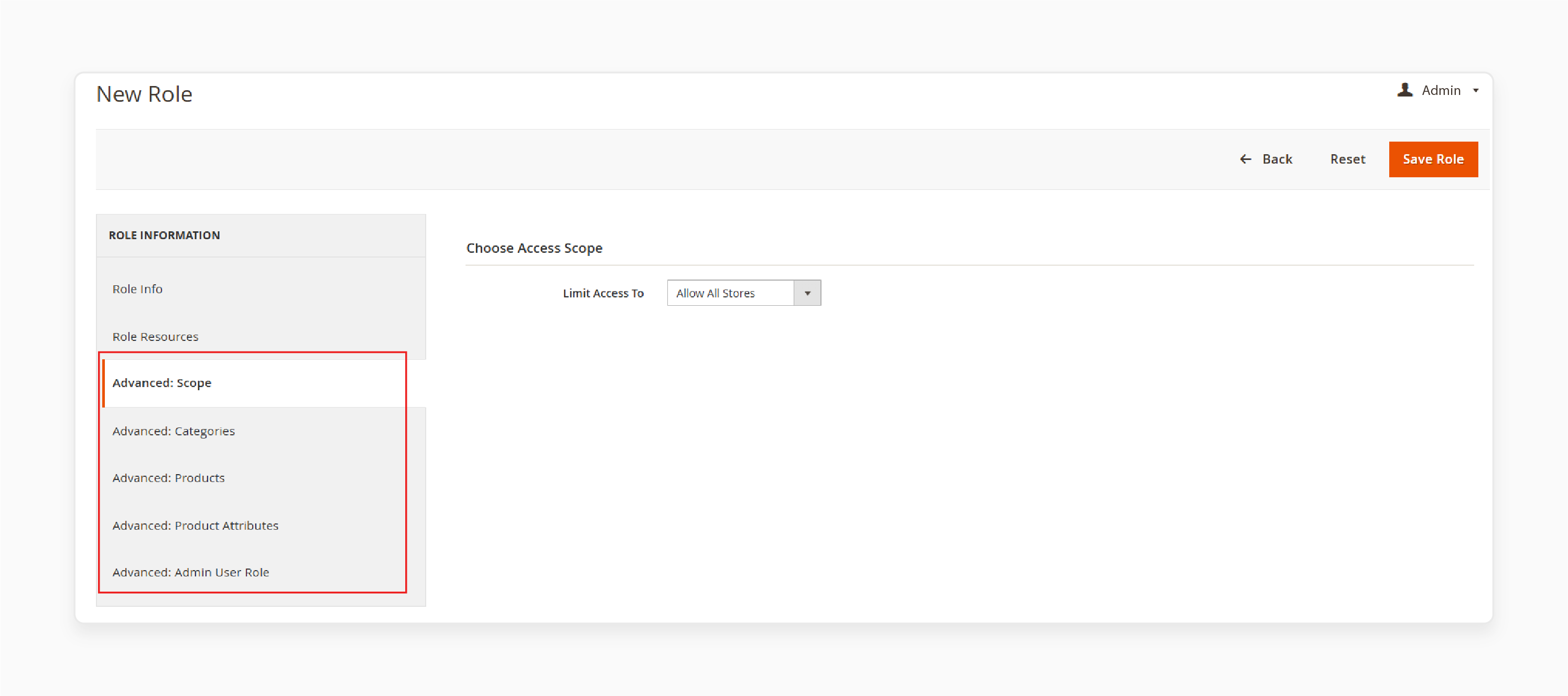
-
Advanced: Scope to limit access to stores/websites
-
Advanced: Categories to limit access to product categories
-
Advanced: Products to limit access to products
-
Advanced: Product Attributes to limit access to attributes
-
Advanced: Admin User Role to configure user creation permissions
-
Step 10: Test Your Security Configuration

-
Log out of your admin panel
-
Try to log in with the configured security measures
-
Verify reCaptcha works on protected forms
-
Check that two-factor authentication prompts for security code
-
Make sure you log in admin actions in the system
Common Conflicts Associated With Magento 2 Security Suite
1. Advanced Permissions ACL Conflicts
-
Core modifications create unpredictable behaviors with
acl.xmlmodifications. Several hooks intoisAllowed()lead to permission check failures. -
Granular rules increase complexity in
\Magento\Catalog\Model\ResourceModel\Product\Collection. Permission filters degrade collection loading withjoinField()operations. -
Security risks emerge when
_isAllowed()returns incorrect values. Operational blockages occur when$subject->isAllowed($resource)fails. -
Admin grids break when
ui_componentXML conflicts with permission checks. ACL conflicts between<resource>definitions create debugging nightmares. -
Performance degradation impacts admin responses during collection filtering. Complex
WHEREconditions add overhead togetSelect()queries.
2. Admin Action Log Integration Problems
-
Event observer chains become unstable with several
<observer>. Execution order issues indi.xmlprevent proper logging functionality. -
Unconventional data modifications bypass
$observer->getEvent()->getData()mechanisms. DirectINSERT/UPDATEqueries create incomplete audit trails. -
Restoration features assume a complete state in
log_dataJSON. ComplexEAVattributes complicate state restoration. -
Observer conflicts break the core
beforeSave()andafterSave()operations. The side effects cascade throughInterceptorclass method chains. -
Performance impacts occur when many
Magento\Framework\Event\Observerinstances fire. Save operations slow with severalaroundplugins active.
3. Google reCaptcha Implementation Weaknesses
-
Dynamic form loading breaks static
.form-loginselector bindings. Forms loaded via$.ajax()miss initial DOM detection. -
JavaScript frameworks render forms outside jQuery's
$(document).ready()scope. ReactuseEffect()components bypass traditional detection methods. -
POST endpoint targeting fails with several
/customer/account/createpost/forms. Same-URL forms lackform_keydifferentiation mechanisms. -
Form submission blocks frustrate legitimate user
checkout.submit()attempts. Silent binding failures exposecontact/index/postto bots. -
Custom integration requires
requirejs-config.jsadditions for complex frontends. Theme updates break.action.submitCSS selector dependencies.
4. Two-Factor Authentication Integration Challenges
-
Alternative login methods conflict with the standard
Authenticate.phpflow. SAML redirects break during<observer>modifications. -
API access requires handling for
rest/V1/integration/admin/tokenendpoints. Cron scripts fail without$this->auth->processAuth()handling. -
Login controllers clash when several plugins adjust
execute()methods. Thearoundplugin collision creates unpredictable authentication behavior. -
Security bypasses happen through unprotected
adminhtml/auth/loginpaths. Inconsistent_validateAdminCredentials()creates vulnerability gaps. -
CLI operations fail with
bin/magentouser-context requirements. Deployment scripts break without proper--auth-tokenhandling.
5. GeoIP Database Dependencies
-
External database requirements create
GeoLite2-City.mmdbdependencies. MaxMind API changes breakReader->get()location detection. -
PHP extensions must exist for
GeoIp2\Database\Readerfunctionality. MissingbcmathorGMPextensions disable core features. -
Login latency increases with each
getCountryIsoCode($ipAddress)call. Admin sessions suffer fromReader->city($ip)database searches. -
Database updates fail due to
curl_exec()or file permission issues. Outdated GeoIP data affects$record->country->ISOCodeaccuracy. -
Server resource consumption increases during concurrent admin logins. High-traffic admin panels experience slowdowns during GeoIP operations.
Troubleshooting Identified Magento 2 Security Suite Conflicts
1. Resolving Advanced Permissions ACL Conflicts
| Problem Area | Resolution Strategy | Specific Actions & Considerations |
|---|---|---|
Core modifications (acl.xml) |
Plugin Prioritization & Defensive Coding | Use sortOrder in di.xml. Do it for plugins targeting ACL classes (e.g., Magento\Framework\AuthorizationInterface). Prefer before/after plugins over around plugins. Audit custom modules adjusting acl.xml for overlaps. |
| Granular rules (Collections) | Query Optimization & Caching | Analyze generated SQL (getSelect()->__toString()) for permission filters. Add database indexes for filtered attributes (e.g., product_owner_id). Cache resolved permissions per admin user session. Profile collection loading. |
Security risks (isAllowed) |
Debugging & Testing | Use Xdebug to trace isAllowed() calls and plugin execution. Set integration tests for critical role permissions. Add logging around permission checks during development/staging. |
Admin grids (ui_component) |
Component Data Provider Analysis | Inspect di.xml for preferences/plugins on UI component data providers (DataProvider). Keep ACL checks within data providers correct. Debug data source requests in the browser's network tab. |
| Performance degradation | Profiling & Targeted Optimization | Use Magento Profiler or tools like Blackfire. Identify ACL checks or collection loading bottlenecks. Refactor complex permission logic. Match database indexes to WHERE clauses from permission filters. |
2. Fixing Admin Action Log Integration Problems
| Problem Area | Resolution Strategy | Specific Actions & Considerations |
|---|---|---|
| Event observer chains | Explicit Ordering & Plugin Preference | Define sortOrder for observers in events.xml and plugins in di.xml. Prefer plugins for predictable execution flow. Use Xdebug to verify the observer/plugin call stack and sequence. |
| Unconventional modifications | Enforce Model Usage & Low-Level Hooks | Enforce data changes via Magento models/repositories in code reviews. If direct SQL remains necessary, trigger logging events. Or, use resource model/adapter plugins. |
Restoration features (EAV) |
Logging & Type Handling | Keep logged data (log_data) with entity_id, attribute_code, old/new values, and type information. Set restoration logic that handles EAV backend types. Test restores. |
| Observer conflicts | Use less Logic & Graceful Handling | Keep observer/plugin logic concise. Use try-catch blocks within observers/plugins to prevent chain halts. Log errors encountered in handlers. |
| Performance impacts | Profiling & Asynchronous Consideration | Profile save operations (model_save_before/after). Adjust logging logic. Queue log data via Magento\Framework\MessageQueue for asynchronous processing if requirements permit. |
3. Strengthening Google reCaptcha Implementation
| Problem Area | Resolution Strategy | Specific Actions & Considerations |
|---|---|---|
| Dynamic form loading (AJAX) | JavaScript Event Handling & Mutation Observers | Trigger reCaptcha initialization via custom JS events after AJAX content loads. Use MutationObserver to detect forms added to the DOM. Use mage/apply/bindings. |
| JavaScript frameworks | Framework-Specific Integration | Create wrapper components (React/Vue/Alpine) for reCaptcha. Use framework lifecycle hooks (useEffect, mounted) to initialize reCaptcha. Confirm tokens via AJAX calls to module endpoints. |
| POST endpoint targeting | Unique Form Identifiers & Backend Logic | Add unique hidden fields to forms submitting to the same URL. Adjust backend validation to check identifiers with reCaptcha tokens. |
| Submissionfm blocks/Failures | JS Error Handling & Debugging | Use try-catch and reCaptcha API callbacks (error-callback, expired-callback). Check browser console/network tab for errors. Provide user feedback on validation failure. |
| Custom integration | Stable Selectors & Documentation | Use stable parent selectors. Avoid theme-dependent classes. Document custom JS. Test reCaptcha after frontend updates. |
4. Overcoming Two-Factor Authentication Integration Challenges
| Problem Area | Resolution Strategy | Specific Actions & Considerations |
|---|---|---|
| Alternative login methods | Compatibility Modules & Plugin Coordination | Develop plugins targeting [Third_Party] 2FA and alternative auth module controllers/logic. Use sortOrder to check 2FA after primary auth succeeds. Analyze both modules. |
| API access / Cron | Token-Based Auth & Conditional Logic | Use Magento integration tokens for API access. Check [Third_Party] configuration to disable 2FA for user roles or IP addresses. |
| Login controllers | Plugin Ordering & Minimal Logic | Define sortOrder for plugins on login controllers (Magento\Backend\Controller\Adminhtml\Auth\Login). Keep plugin logic minimal. |
| Security bypasses | Audit Entry Points & Consistent Application | Audit admin authentication controllers and DI preferences. Apply 2FA checks to all admin entry points. Test edge cases and alternative login URLs. |
| CLI operations | Dedicated Users or Service Accounts | Run CLI commands as a dedicated admin user without 2FA if security policies permit. Explore token-based CLI authentication if supported. |
5. Mitigating GeoIP Database Dependencies
| Problem Area | Resolution Strategy | Specific Actions & Considerations |
|---|---|---|
| External database | Error Handling & Monitoring | Use try-catch around GeoIP lookups (Reader->get(), Reader->city()). Track MaxMind updates. Fallback to log "Unknown Location" on failure. |
| PHP extensions | Environment Provisioning & Checks | Install ext-bcmath or ext-gmp via server configuration. Add extension checks to deployment scripts or Magento readiness checks. Include in composer.json require. |
| Login latency | Caching & Asynchronous Lookups | Cache IP-to-location results in Redis/Varnish/memory (keyed by IP) with TTL. Perform asynchronous GeoIP lookups. Do it post-login via queue if you don’t need real-time blocking. |
| Database updates | Permissions & Cron Scheduling | Set the web server user with write permissions to var/[Third_Party]/geoip/. Configure and track cron jobs for updates. Check firewall rules for MaxMind access. |
| Server resource consumption | Caching & Resource Allocation | Cache lookups. Keep server with RAM and disk I/O (SSD) requirements for .mmdb access. Profile during peak admin usage. |
FAQs
1. What are the most critical security vulnerabilities in Magento 2?
SQL injection attacks risk Magento store data. Cross-site scripting targets checkout pages. Hackers attempt admin panel brute force. Outdated extensions create security gaps. Payment information theft drives most attack goals.
2. How does two-factor authentication impact admin user experience?
Two-factor authentication adds seconds to login time. Admins need phones for code generation. Time drift causes code regeneration issues. White-listed IPs bypass 2FA from trusted locations. Users adapt to minimal workflow disruption.
3. Can Magento 2 Security Suite protect against zero-day exploits?
Security suites limit damage from unknown threats. Advanced logging identifies suspicious activities. IP rules block unauthorized access attempts. Alerts notify admins about unusual behavior. Zero-day protection remains impossible, but risks decrease.
4. Are security logs affecting database performance?
Security logs consume database space. Auto-cleaning stops excessive table growth. Track log tables in busy stores. Indexes boost log query speed. Adjust retention periods for server needs.
5. How do custom modules interact with Security Suite permissions?
Custom modules need proper ACL setup. Security suites block incorrect permission codes. Developers must follow Magento permission rules. Testing reveals module integration conflicts. Advanced permissions cause unexpected access limits.
6. What security measures should complement a Magento 2 Security Suite?
Apply security patches to protect your platform. Set firewalls to block bad traffic. Encrypt databases with sensitive data. Scan for new security issues often. Regular backups allow recovery when protections fail.
Summary
Magento 2 Security Suite protects against e-commerce threats. Google reCaptcha, action logging, and 2FA create defense layers. The suite adds tools to Magento's security features. Consider the below main points from the tutorial for the best results:
-
Set up Google Invisible reCaptcha for forms. It blocks bots from customer forms. Users enjoy smooth form interaction.
-
Turn on admin action logging for records. The system tracks all admin actions. Timestamps and user details create accountability.
-
Add two-factor authentication for all admins. The extra layer secures admin access. Password theft becomes less harmful.
-
Create advanced permissions for admin roles. Limit staff access to critical areas. Control who edits products and categories.
-
Set automated security maintenance and alerts. Clean logs to optimize database space. Get alerts when attacks happen.
Managed Magento Hosting resolves security suite installation errors to protect your store.





