
AWS WAF Magento: Configuration and Best Practices
Are you looking to protect your Magento 2 store from cyber attacks and threats? AWS WAF Magento integration is a security solution offered by Amazon Web Services. It protects web applications from potential threats and attacks.
In this tutorial, we will explain how to integrate the web application firewall by AWS with your Magento store.
Key Takeaways
-
Learn how AWS WAF can tailor security for Magento 2 ecommerce sites using rules.
-
Discover how WAF integrates with services like Amazon CloudFront and Application Load Balancers to enhance security.
-
Find out how to set up and manage Web ACLs to protect your Magento resources effectively.
-
Understand the importance of employing managed rules and custom rules to guard against evolving threats.
-
Gain insights into maintaining compliance and securing sensitive data with AWS WAF for Magento 2 sites.
Benefits of AWS Web Application Firewall
-
AWS Web Application Firewall is a security service by Amazon Web Services. It protects web applications from web exploits and vulnerabilities.
-
It allows users to create customized rules that block, allow, or monitor web requests based on conditions. These conditions include IP addresses, HTTP headers, HTTP body and URI strings, and SQL injection.
-
These rules manage specific types of threats that compromise the security of Magento sites.
-
AWS WAF is integrated directly into Amazon CloudFront, the Application Load Balancer, and Amazon API Gateway. It makes it easier to deploy and manage without affecting the existing infrastructure.
-
The Amazon Web Services WAF operates at the application layer. It inspects HTTP and HTTPS traffic before it reaches the application. It effectively filters out malicious requests based on the rules defined.
Integration with AWS Services
1. Integration with Amazon CloudFront
-
Amazon Cloudfront is a CDN service that delivers data, videos, applications, and APIs to customers globally. It does this with low latency and high transfer speeds.
-
When AWS WAF is integrated with CloudFront, the WAF rules are evaluated at the edge locations. It means that malicious requests can be blocked before they reach the application servers.
-
You attach a web ACL (Access Control List) created in AWS WAF to a CloudFront distribution.
-
A web ACL is a set of rules that govern how traffic is handled when accessing your Magento open source web applications.
-
The rules in this web ACL will then inspect all incoming requests to the distribution. Based on the conditions set in the rules, AWS WAF will allow, block, or count the requests.
-
This integration helps protect against DDoS attacks. It reduces the server load by filtering out malicious traffic at the edge and enhances overall security.
2. Integration with Application Load Balancers (ALB)
-
Application Load Balancers distribute incoming application traffic across many targets and availability zones.
-
This increases the fault tolerance of your applications. Integrating AWS WAF with ALB allows the rules to be applied directly to the traffic going to the load balancer.
-
A web ACL is associated with one or more listeners on the ALB. Whenever a client requests the ALB, AWS WAF evaluates the request based on the rules in the associated web ACL.
-
This integration ensures that clean traffic is passed to the application. It also allows for security control based on the content of the HTTP messages.
3. Integration with Amazon API Gateway
-
Amazon API Gateway is a service that makes it easy to create, publish, maintain, monitor, and secure APIs. By integrating AWS WAF with API Gateway, you can protect your APIs from common web exploits and bot attacks.
-
Similar to the other integrations, you attach a web ACL to an API stage in API Gateway. AWS WAF then inspects the incoming API calls based on the rules defined in the web ACL.
-
This setup protects the backend services from being exploited by attacks such as SQL injection and XSS. These are common in API-based applications. It also helps manage quotas and limit excessive API calls, which can be a vector for attacks.
Steps to Set Up AWS WAF in Magento
-
Begin by setting up an AWS account if you still need to get one.
-
Navigate to the AWS WAF console to start configuring your web application firewall.
-
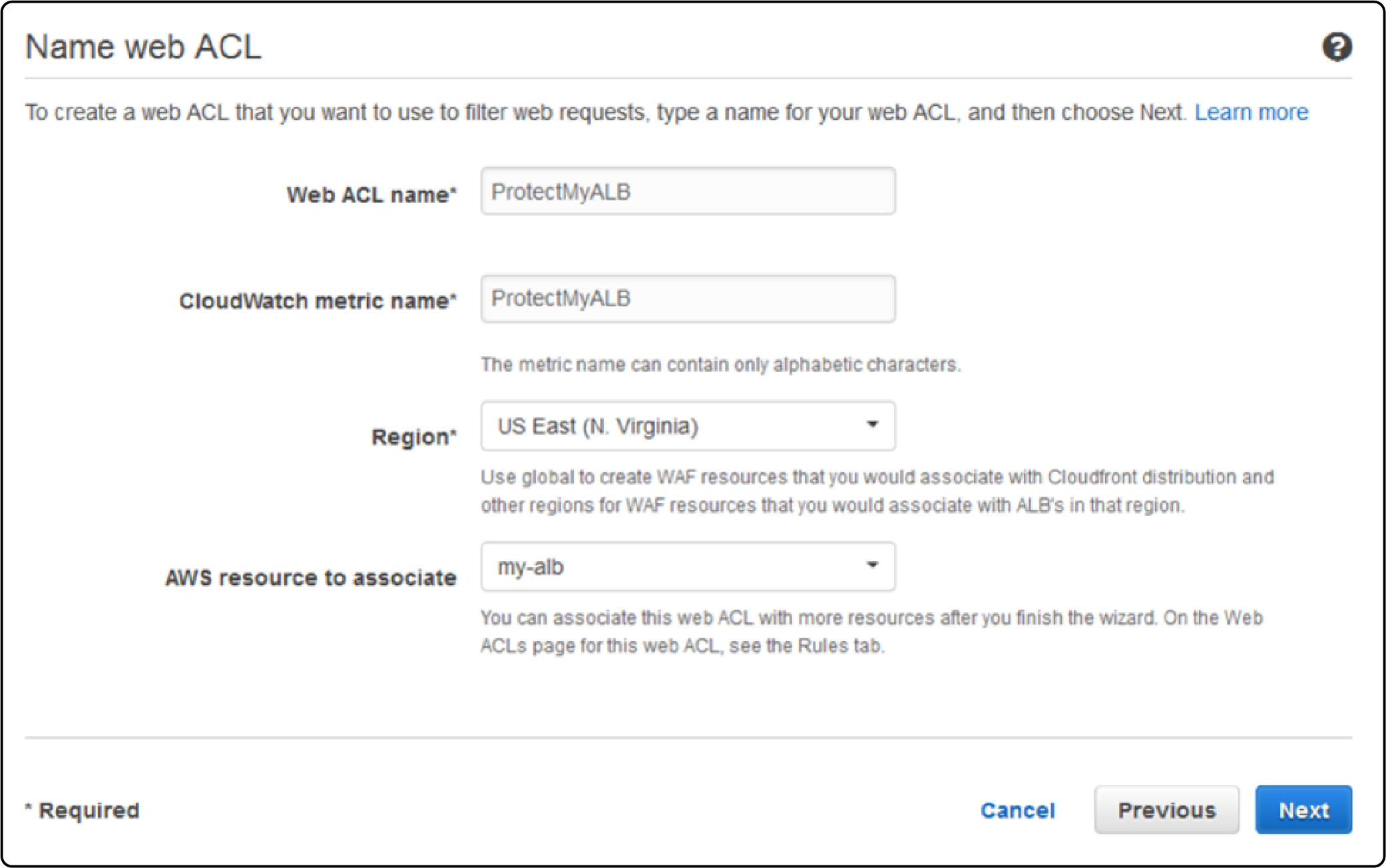
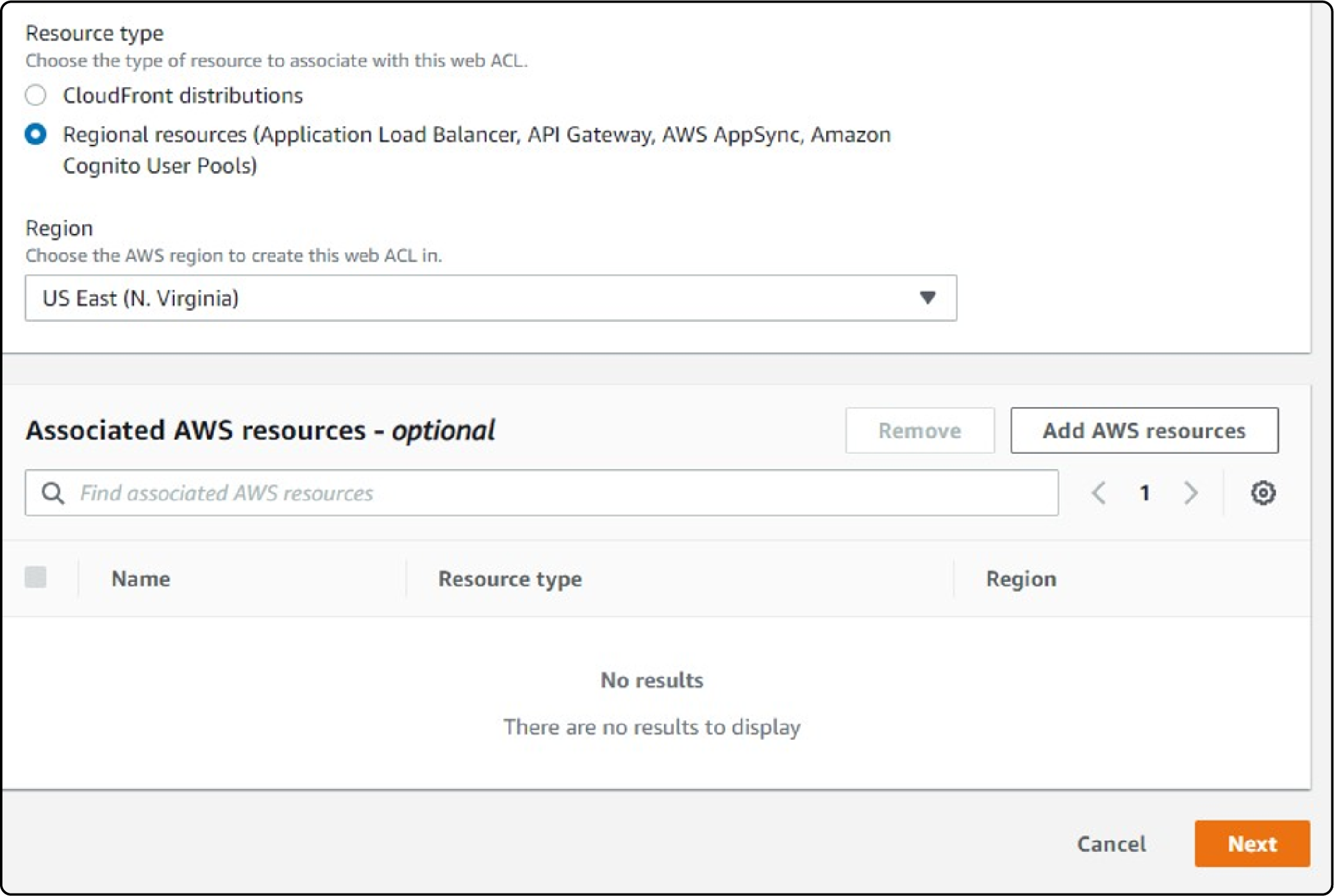
Create a Web ACL in the AWS WAF console and associate it with the AWS resources running your Magento application.
-
Specify the resources that you want to protect, such as the URLs of your Magento store.
-
AWS WAF can be applied to either an Application Load Balancer or an Amazon API Gateway API.
-
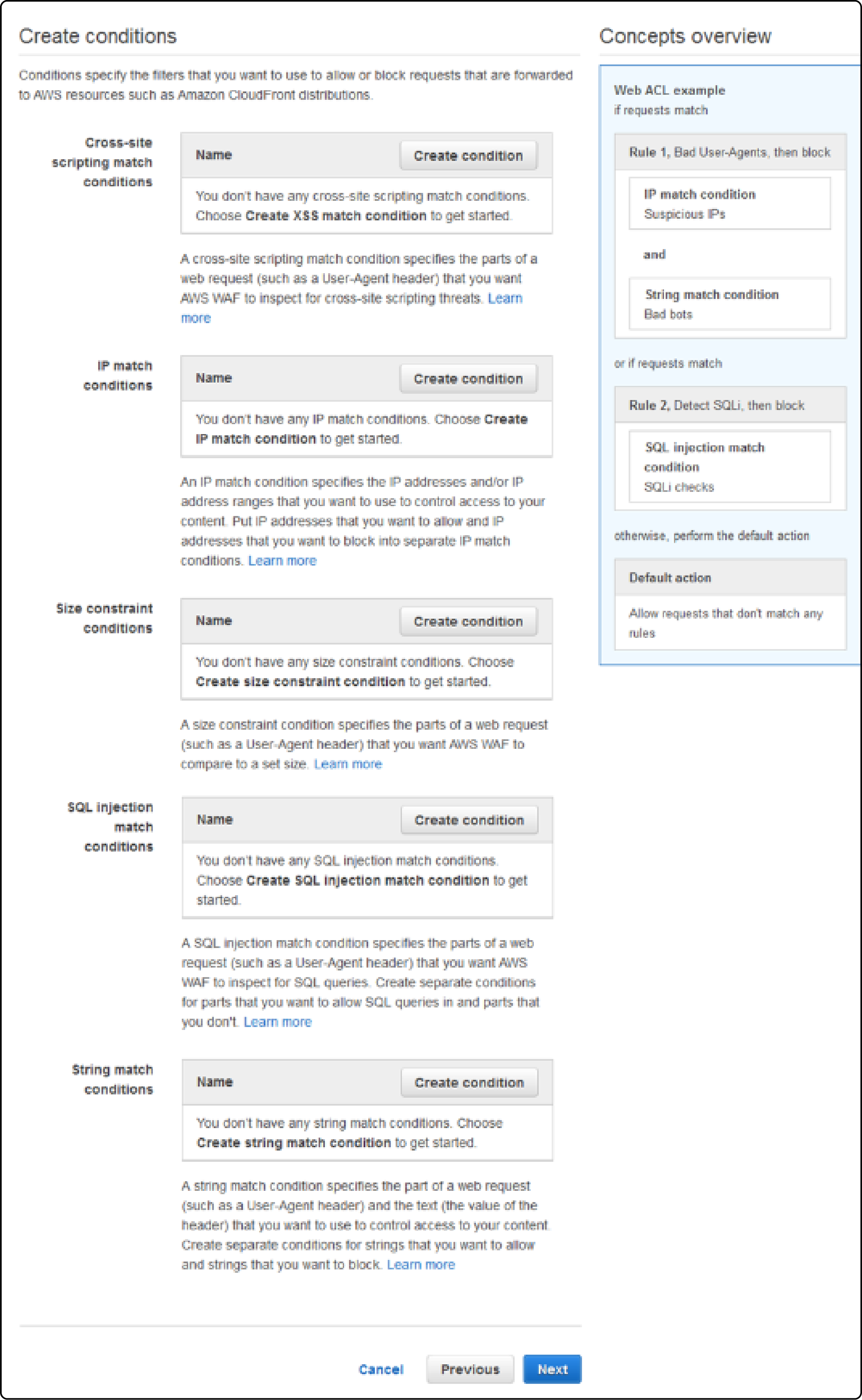
Create rules based on common threats to Magento stores. These include SQL injection or cross-site scripting (XSS).
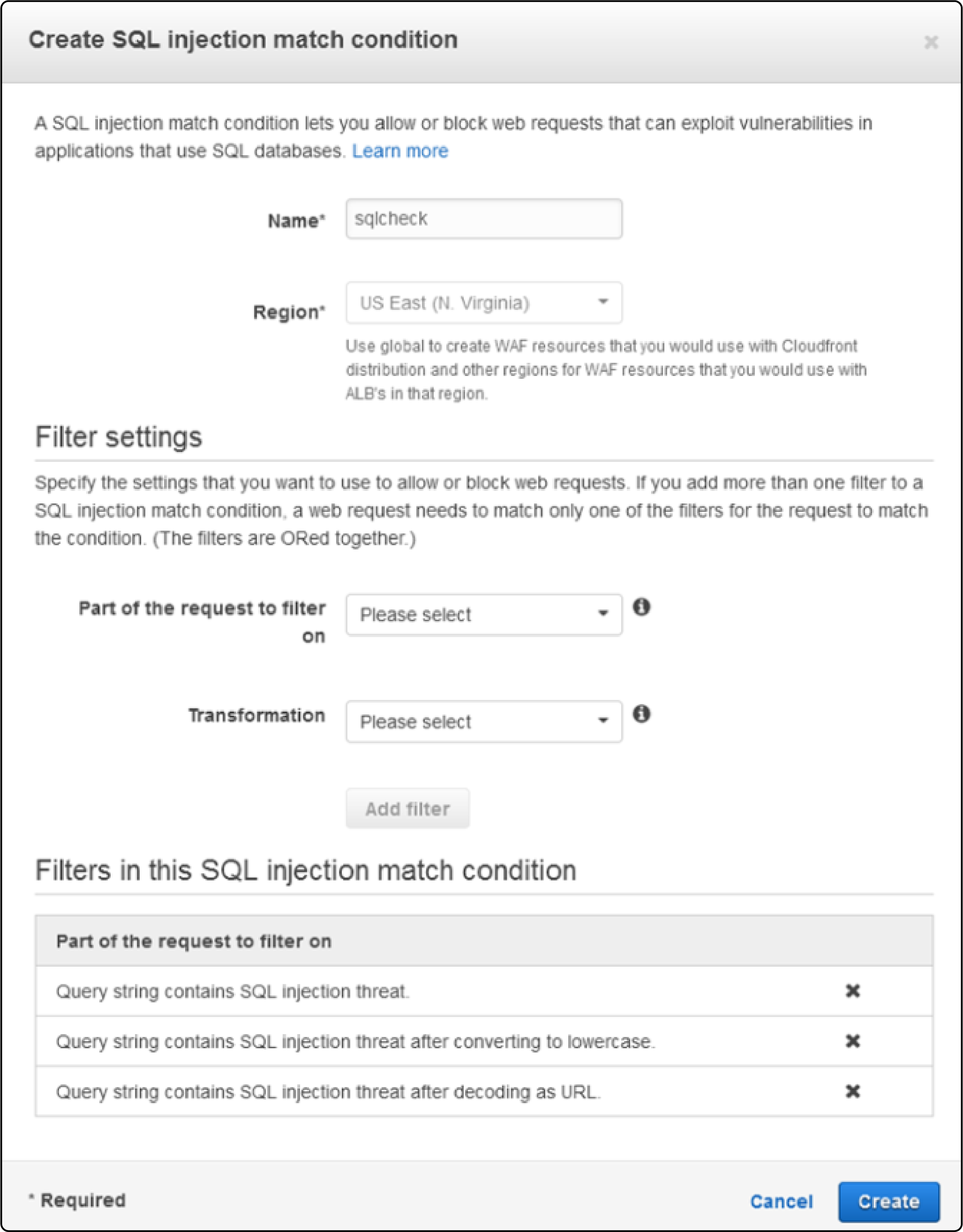
-
Use conditions in AWS WAF to specify the parts of requests that AWS WAF inspects. These include URI strings, query strings, headers, or methods (GET or POST).
-
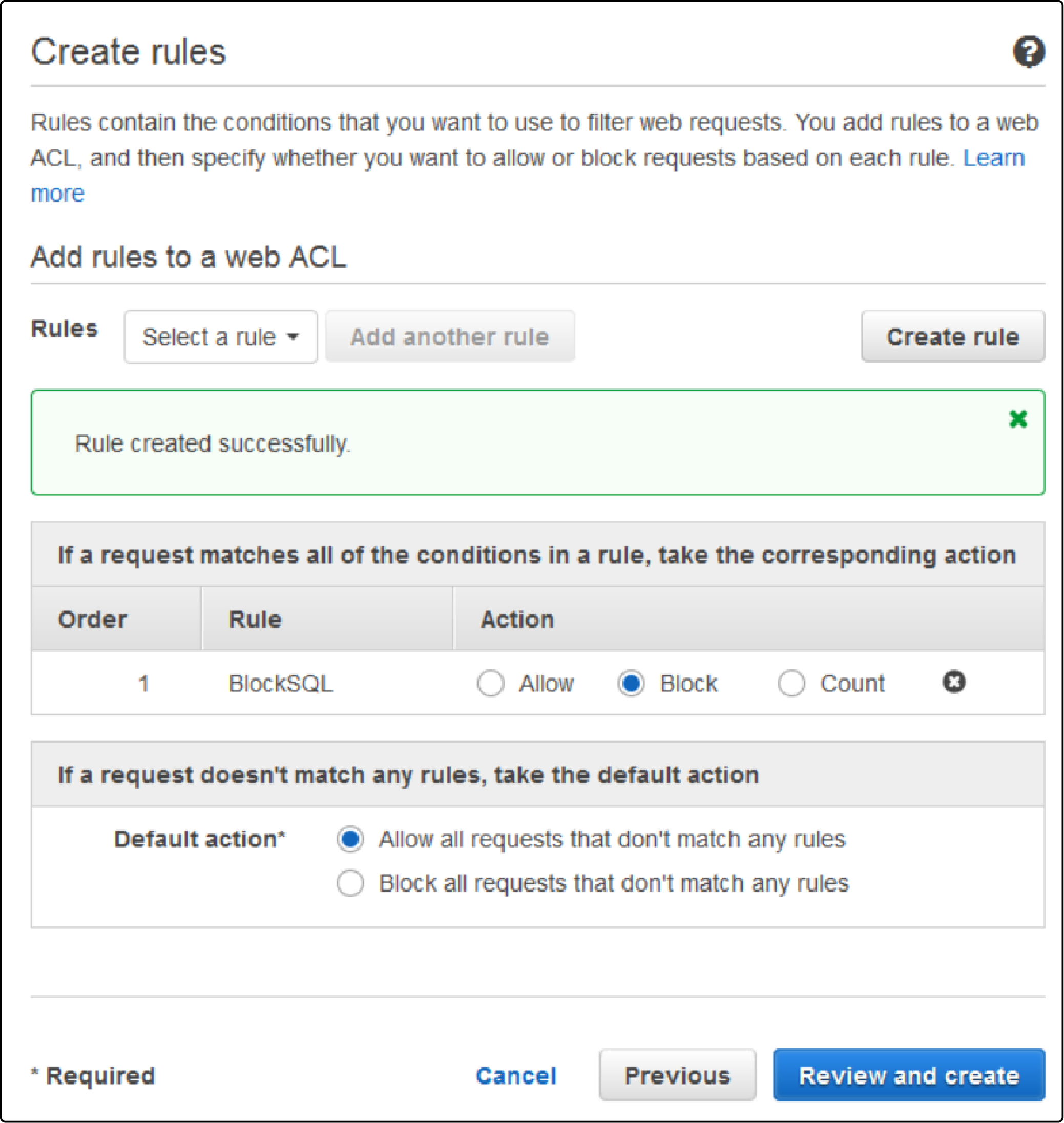
After creating rules, add them to your web ACL and set an action for each rule—allow, block, or count. The 'count' action helps you monitor the impact of the rules on traffic without enforcing them.
-
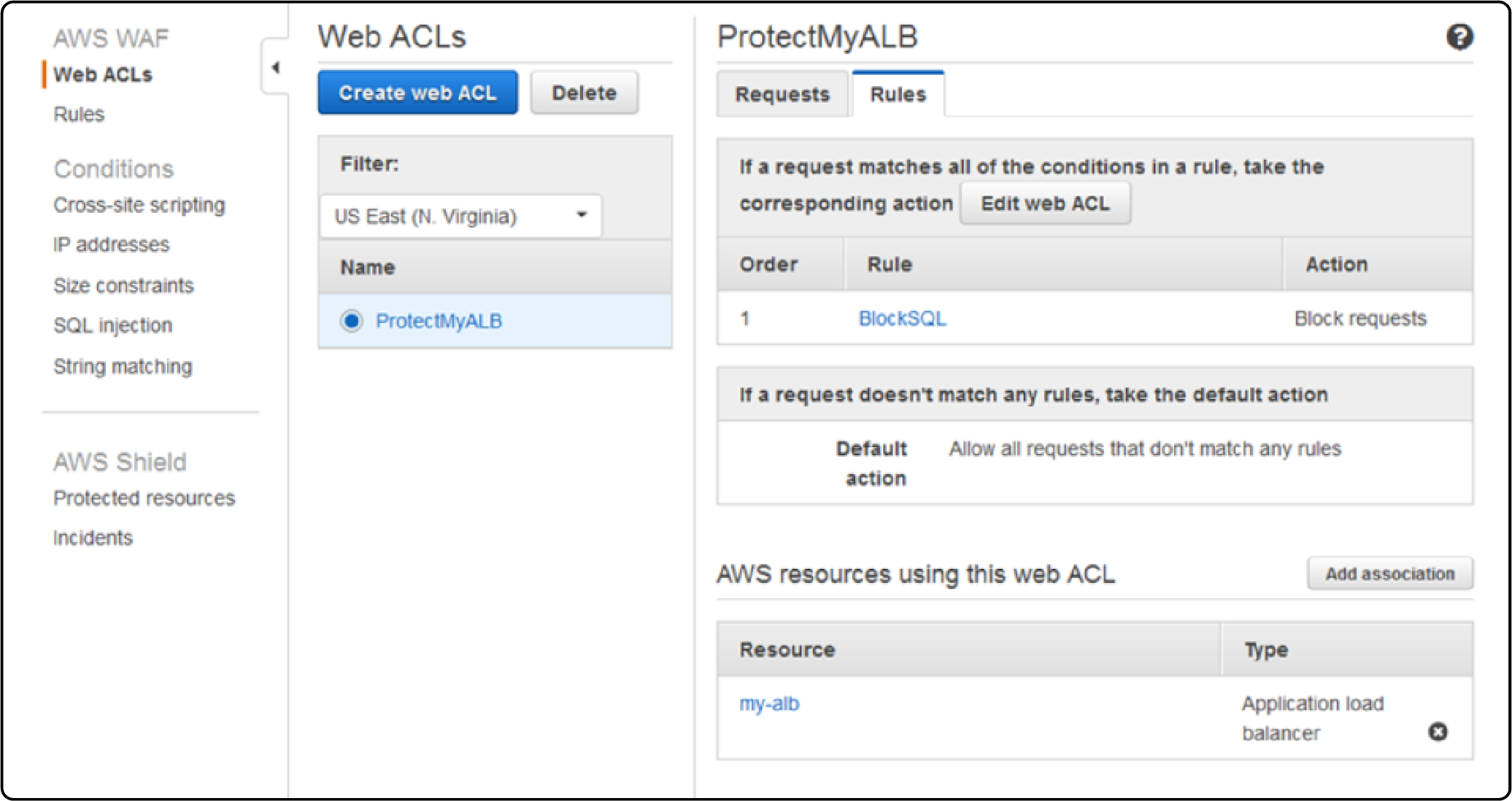
Associate the web ACL with your resource, such as a specific CloudFront distribution that serves your store. This step finalizes Magento security, enforcing your rules for all incoming traffic.
Best Practices for AWS WAF and Magento 2
1. Employ Managed Rules
-
AWS WAF provides managed rule sets that are designed to protect web applications from common attacks. These include the OWASP Top 10 security risks. The OWASP Top 10 is a standard awareness document listing the most critical security risks to web applications.
-
These managed rules include protections against threats like:
-
Attackers insert malicious SQL code into application queries to the database. The managed rules look for patterns that indicate SQLi attempts in the HTTP requests.
-
Attackers inject client-side scripts into web pages to steal data or perform actions on behalf of users. The rules detect common XSS patterns and block malicious requests.
-
Other OWASP risks include broken authentication, sensitive data exposure, XML external entities, broken access control, etc.
-
-
AWS automatically updates these managed rules to ensure protection against the latest threats.
-
It allows you to quickly add a base level of protection to your web applications. AWS partners, like Fortinet and Cloudbric, offer managed rules specifically for Magento stores.
-
These rules take into account Magento-specific vulnerabilities and attack patterns. You can easily subscribe to these managed rules from the AWS Marketplace and directly add them to your web ACLs.
2. Custom Rules for Specific Threats
You should also customize AWS WAF rules based on your specific Magento store requirements. Some examples of custom rules:
-
Geo-blocking rules: You can use geo-match conditions to allow or block web requests based on the geographical location of the client. It is useful if your Magento store needs to comply with regional regulations and licensing restrictions.
-
Size constraint rules: These rules check the length of specific parts of the HTTP request, like the body, query string, URI, or headers. You can set size limits to block requests where the length exceeds normal expectations. It could indicate an attack attempt like buffer overflow or data injection.
-
Refined string and regex matching rules: You can define additional rules looking for strings, regex patterns, and attack signatures that target Magento platforms. It allows you to enforce stricter security policies.
-
Rate-based rules: These limit the number of web requests from a client's IP address over some time. It helps mitigate HTTP flood attacks, brute-force login attempts, and web scraping. You can set different rate limits for different Magento store pages.
-
3. Regular Rule Review and Updates
-
The threat landscape evolves with new attack techniques and the discovery of Magento vulnerabilities.
-
Periodically audit your WAF rules to evaluate their effectiveness. Analyze the requests being logged and blocked by each rule. Remove outdated rules and change existing ones based on changing traffic patterns.
-
Monitor AWS WAF logs and metrics using services like Amazon CloudWatch. The logs capture details about web requests that are analyzed by your WAF rules. CloudWatch helps you track the number of allowed and blocked requests over time. Investigating spikes in blocked requests can reveal new threats and help you refine the rules.
-
Keep up-to-date with the latest Magento security patches and version upgrades. Adjust your WAF rules to protect against newly disclosed vulnerabilities.
-
Subscribe to threat intelligence feeds and security bulletins. It is to stay informed about emerging attack trends. Proactively update your rules to mitigate these threats.
4. Testing and Simulation
-
Adding or modifying WAF rules can accidentally impact legitimate traffic to your Magento store. To minimize disruption, it's important to test new rules before fully enforcing them:
-
Use the "Count" action to set the rules in the initial testing phase. Instead of blocking matching requests, the rule just increments a counter. It allows you to gauge the potential effects of a new rule without impacting real traffic.
-
Implement a staged rollout process for rule changes. For example, start by enforcing a new rule on a small percentage of incoming requests. Gradually increase coverage while monitoring for false positives. You can also test rules on a staging environment that mirrors production traffic.
-
Simulate common attack patterns and verify that the WAF rules detect and block them correctly. Tools like AWS WAF Security Automations and GoTestWAF can help automate the security tests.
5. Secure Magento Specific Endpoints
-
Admin panel pages: These provide access to powerful backend functionality and should be locked down. Put in place strong authentication rules and use rate limiting to prevent brute force attempts.
-
Login and checkout pages are easy targets for credential stuffing, payment fraud, and account takeovers. Use rate-based rules to limit login attempts from an IP address. Enforce strict input validation rules to prevent SQLi, XSS, and other injection attacks.
-
APIs and web services: Magento stores often expose APIs for mobile app integration and third-party services. Protect these endpoints against API security risks like broken authentication, excessive data exposure, and parameter tampering.
6. Compliance and Data Security
- Ensure compliance with relevant regulations (like GDPR and PCI DSS for payment security) through AWS WAF configurations:
-
Data protection: Use rules to prevent data leakage by inspecting and filtering outbound responses.
-
PCI DSS compliance: As Magento stores handle credit card data, specific configurations in AWS WAF can help in meeting PCI DSS requirements, like securing cardholder data.
-
FAQ
1. What is AWS WAF, and how does it protect Magento websites?
AWS WAF is a web application firewall that protects Magento websites. It does this by creating security rules to control bot traffic and filter out specific web application threats.
2. How can AWS WAF Managed Rule Groups benefit Magento 2 module security?
Managed Rule Groups in AWS WAF and managed by AWS security experts, automatically updated to protect Magento sites. It protects sites from web attacks like SQL injection and XSS.
3. Can AWS Shield be integrated with AWS WAF to enhance security for Magento websites?
Yes, integrating AWS Shield Advanced with AWS WAF protects Magento websites. Attacks like distributed denial of service attacks by preventing excessive resource consumption.
4. What are the benefits of using AWS Firewall Manager with AWS WAF for Magento?
AWS Firewall Manager allows full control of web security policies across many Magento websites. It ensures consistent security with AWS support.
5. How does AWS WAF help in complying with security requirements for Magento web applications?
Use AWS WAF to provide compliance support with Magento security requirements. It is done by filtering specific referrers and geo-locations and preventing unauthorized access.
Summary
AWS WAF Magento integration is a secure way to protect your Magento store from different cyber attacks and threats. This tutorial explains how AWS WAF can be configured and integrated with Magento. Here is a short recap:
-
AWS WAF secures Magento 2 sites by allowing customized security rules to block, monitor, or allow web requests based on conditions.
-
It integrates easily with AWS services such as Amazon CloudFront, Application Load Balancers, and Amazon API Gateway.
-
Users can set up Web ACLs in AWS WAF to manage security rules and protect specific AWS resources.
-
Best practices include using AWS-managed rule sets for automated updates against common threats and creating custom rules for specific needs.
-
AWS WAF supports compliance and secures sensitive data to meet regulatory requirements and protect Magento stores.
Choose a managed Magento hosting provider to integrate your ecommerce store with AWS to scale effortlessly.



