
Role of Magento 2 Encryption Key for E-commerce Security
Are you sure your store's sensitive data is properly encrypted and safe from threats? Magento 2 Encryption Key is an important security tool that protects data. It works as a key for Adobe Commerce or Magento, but it has risks like CVE-2024-34102.
This article will cover how to safeguard customers' personal information with industry regulations.
Key Takeaways
-
What are the aspects of an encryption key?
-
Security keys protect private data like passwords and payment info.
-
Find your store’s key is located in the admin panel.
-
Reasons why encryption key is important.
-
List of 8 best practices for managing security keys.
-
Fixing common problems to keep your store running.
What is the Magento 2 Encryption Key?
Magento 2 Encryption Key is a security tool that protects passwords and other sensitive data. It uses a crypt key to lock data in an encrypted string format.
Magento 2 encryption key keeps important data, like passcodes, credit cards, and personal details, safe. It is a cryptographic key that encrypts and uncovers the data. The key ensures that it remains secure and inaccessible to unauthorized users. If someone gets into your database, the encrypted values stay safe.
The security key in Magento is stored in the env.php file. If the original key is compromised or outdated, it's wise to change the key. You can use the encryption key tool to generate a new key or add a new encryption key. This keeps your store safe and meets standards like PCI DSS.
Role of Encryption Keys in Protecting Sensitive Data
1. Encryption Process
Security keys turn readable data into an unreadable format. It protects secure data in Magento, like credit card data and passcodes. This keeps it safe from unauthorized users. During upgrades or Magento migrations, you might need to change the encryption key. It lets the system auto-generate a key for more security.
2. Decryption
Decoding changes protected data back into readable form. Only the right Magento encryption key can do this. For example, when a customer logs in, the system uncovers their data. If you perform a key rotation, Magento keeps the data secure.
3. Security Enhancement
Security keys stop data breaches. Even if someone gets access to protected data, they can’t read it without the decoding key. After you update the security key, remember to re-encrypt any config values using the new key. It keeps the data safe for the stores.
4. Compliance
Security keys help your store meet rules like PCI DSS and GDPR. The ecommerce platform provides tools like the encryption key from the admin panel. It manages your config values using the new key. This helps you meet legal standards for securing personal data.
5. Key Management
Managing security keys protects data. You need to generate, store, and rotate them securely. Magento’s key tool in the admin helps you do this. If the original key might be compromised, it's best practice to change it and re-secure your data. Proper key management prevents security issues.
6. Symmetric and Asymmetric Encryption
When you change the Magento 2 security key during upgrades, update your core_config_data. It helps to avoid issues. It supports both:
-
Symmetric (one key for both encryption and decryption)
-
Asymmetric encryption (two keys: public for encryption, private for decoding).
7. Data Integrity
Security keys also stop data from being altered during storage or transmission. It is important for securing credit card information and personal data. Follow the steps to change the key and re-secure your data to keep it safe. Stay updated with security bulletins for best practices.
Where to Locate the Magento 2 Encryption Key in Your Store?
In Magento 2, the security keys are stored in the env.php file. The file also has settings for your database, which is helpful if you need them when moving your site or changes.
5 Steps to Find Encryption Key:
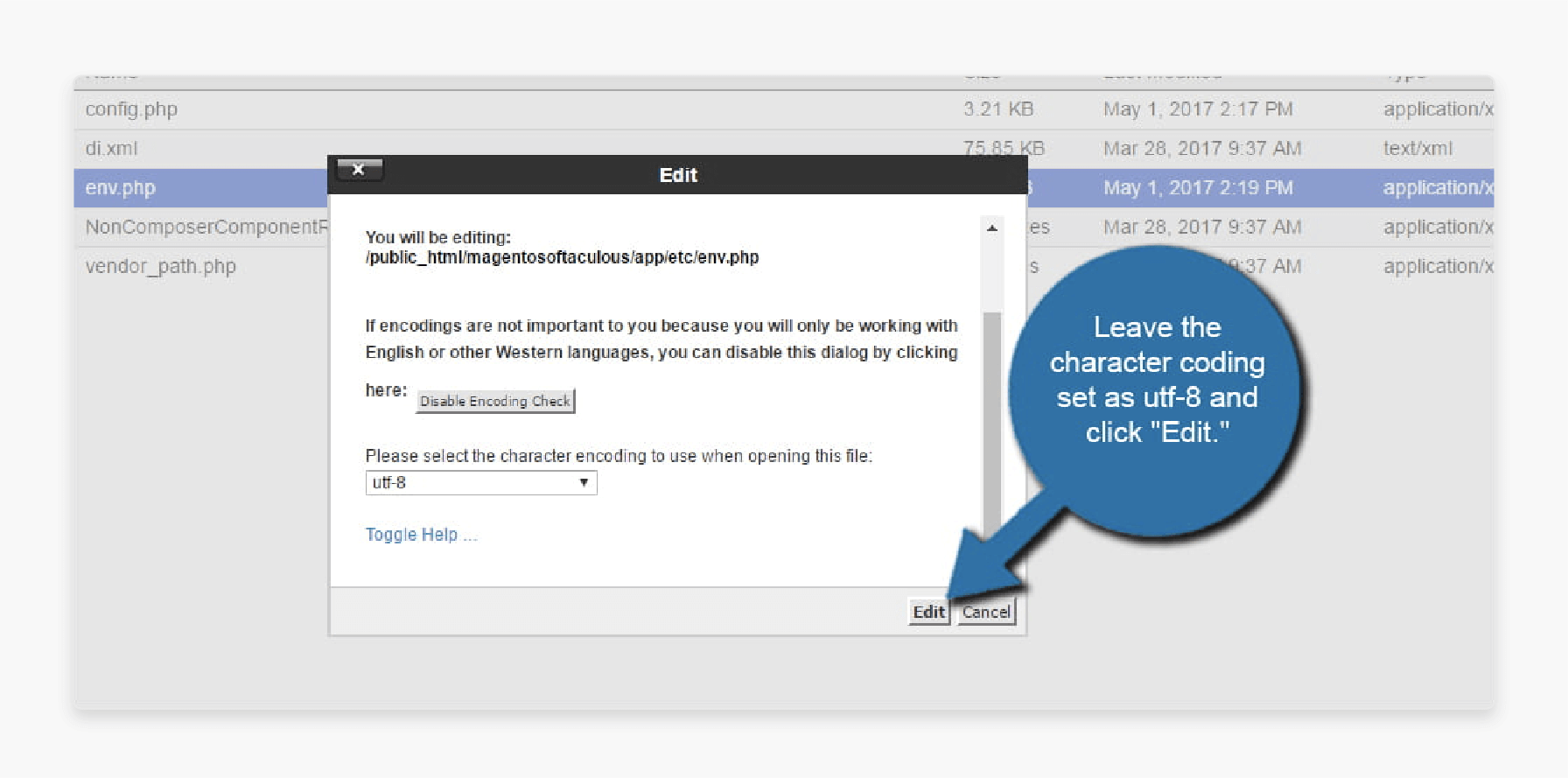
Step 1: Log in to cPanel and click on the "File Manager" tool.
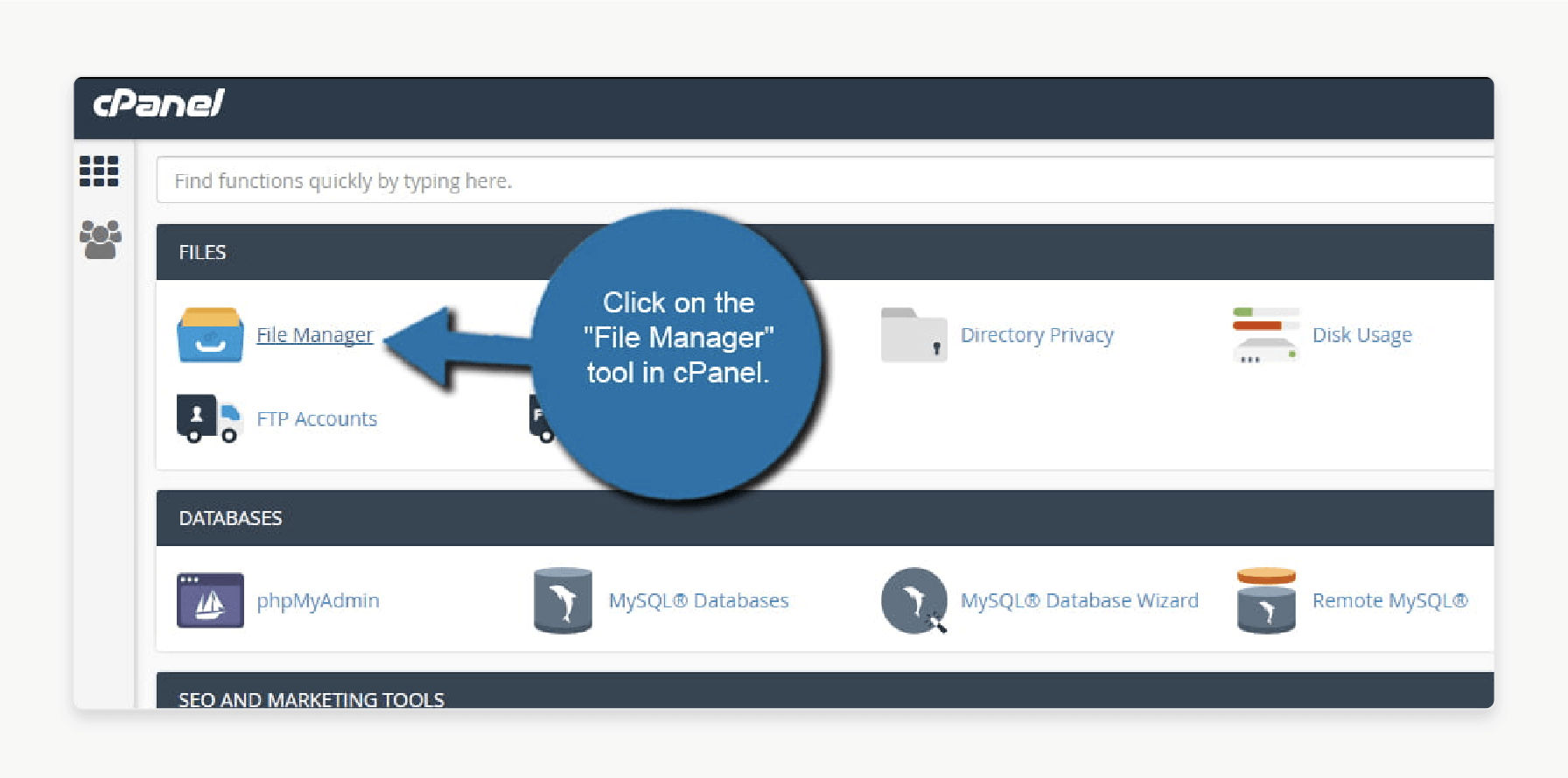
Step 2: Go to the Magento directory by opening the “public_html” folder where your site is stored.
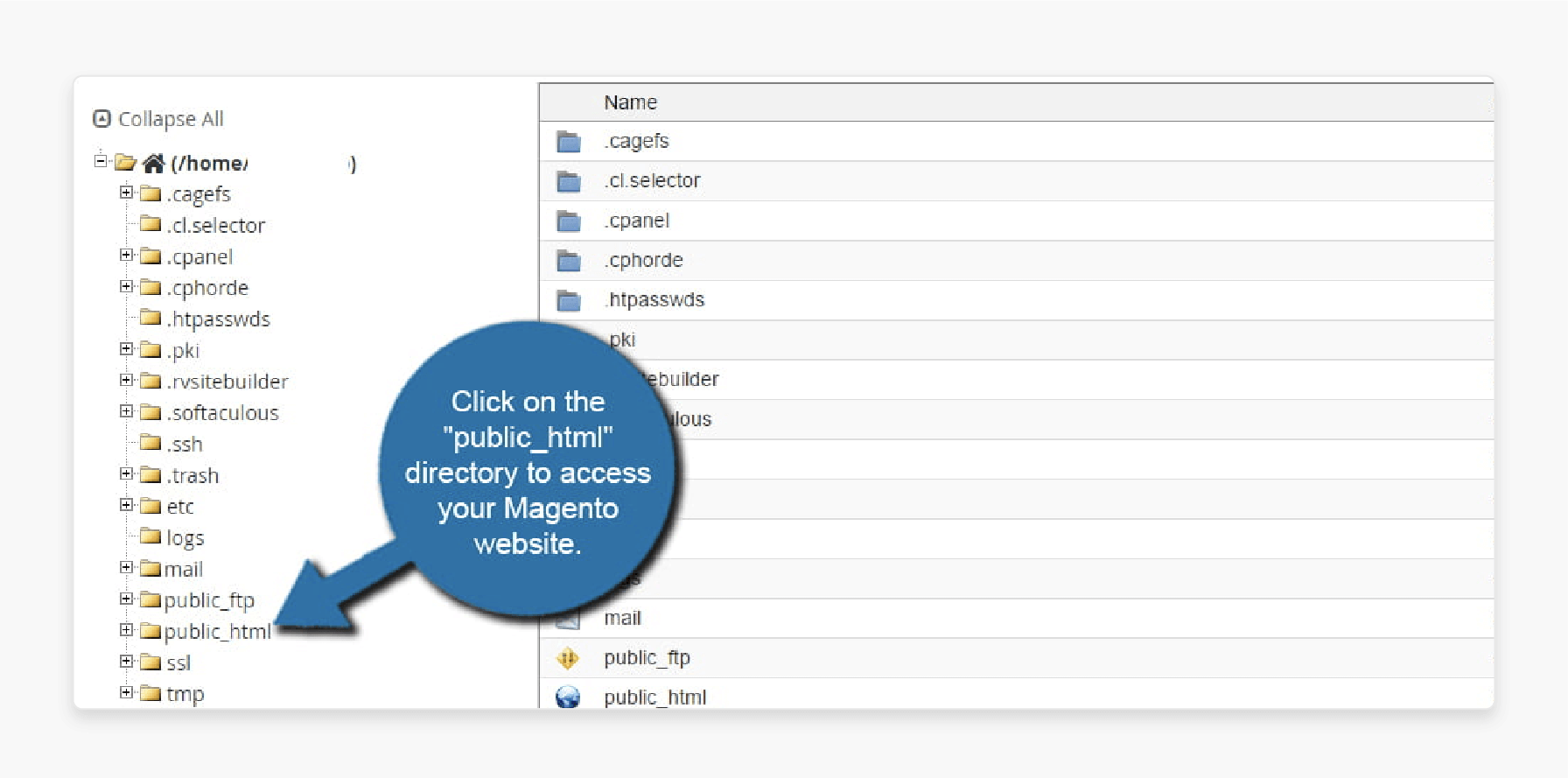
Step 3: Double-click the app folder, then open the etc folder.
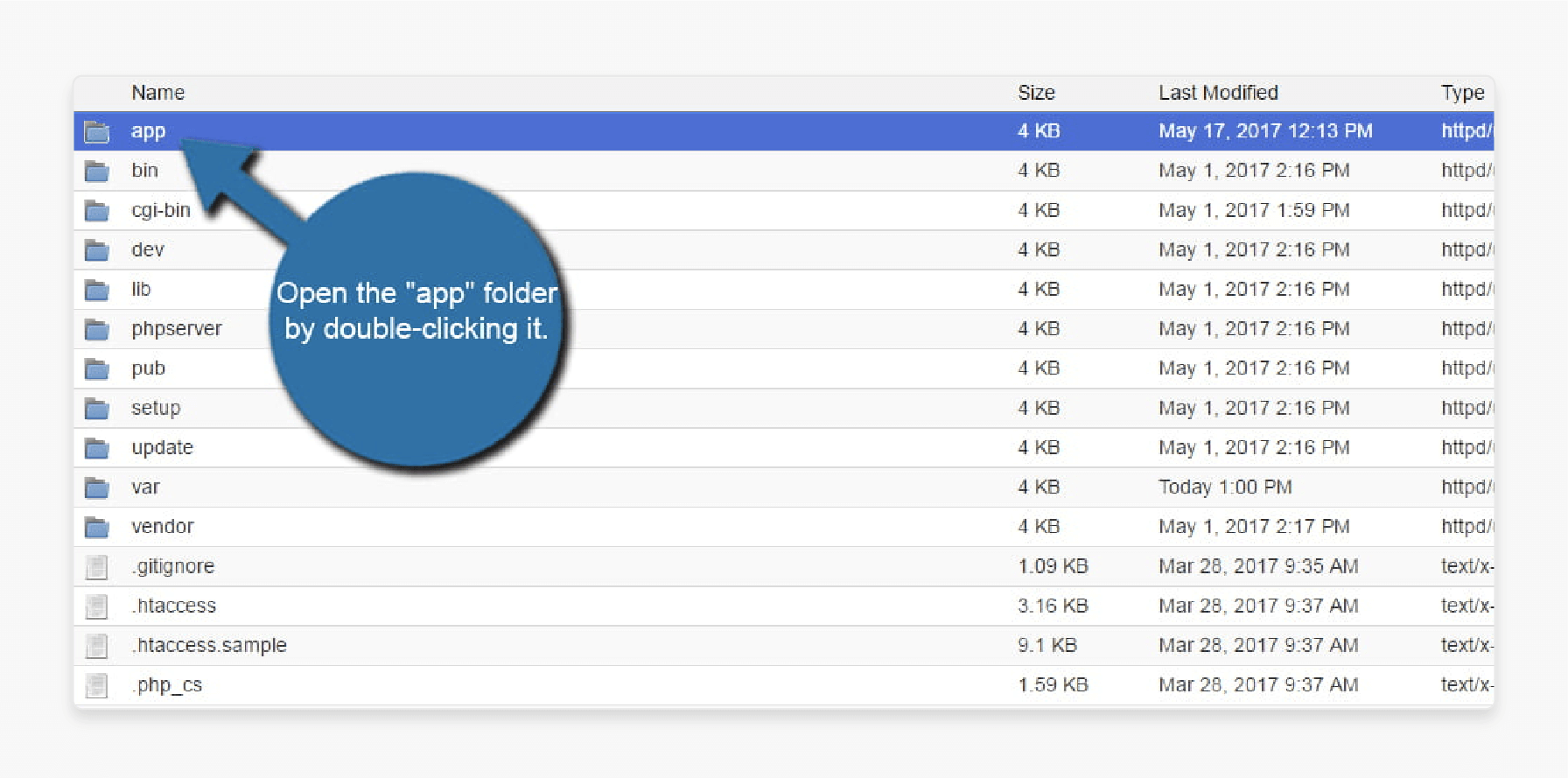
Step 4: Find the env.php file, click it once to highlight it, then click "Edit" in the toolbar.
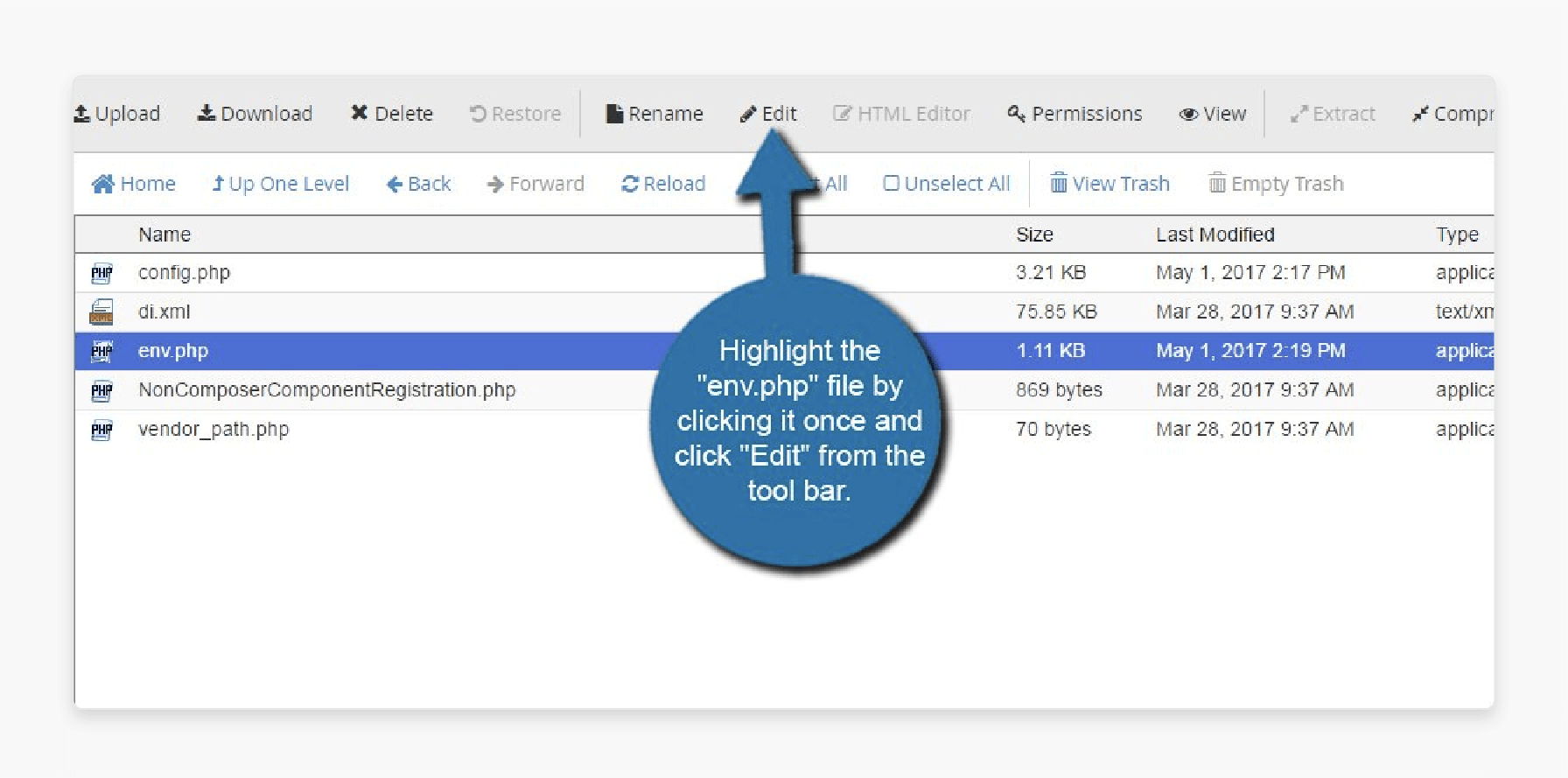
Step 5: When asked, keep the character encoding as utf-8 and click "Edit."
Inside the env.php file, the encryption key is in the crypt array under the line:
'key' => 'your_encryption_key_here'
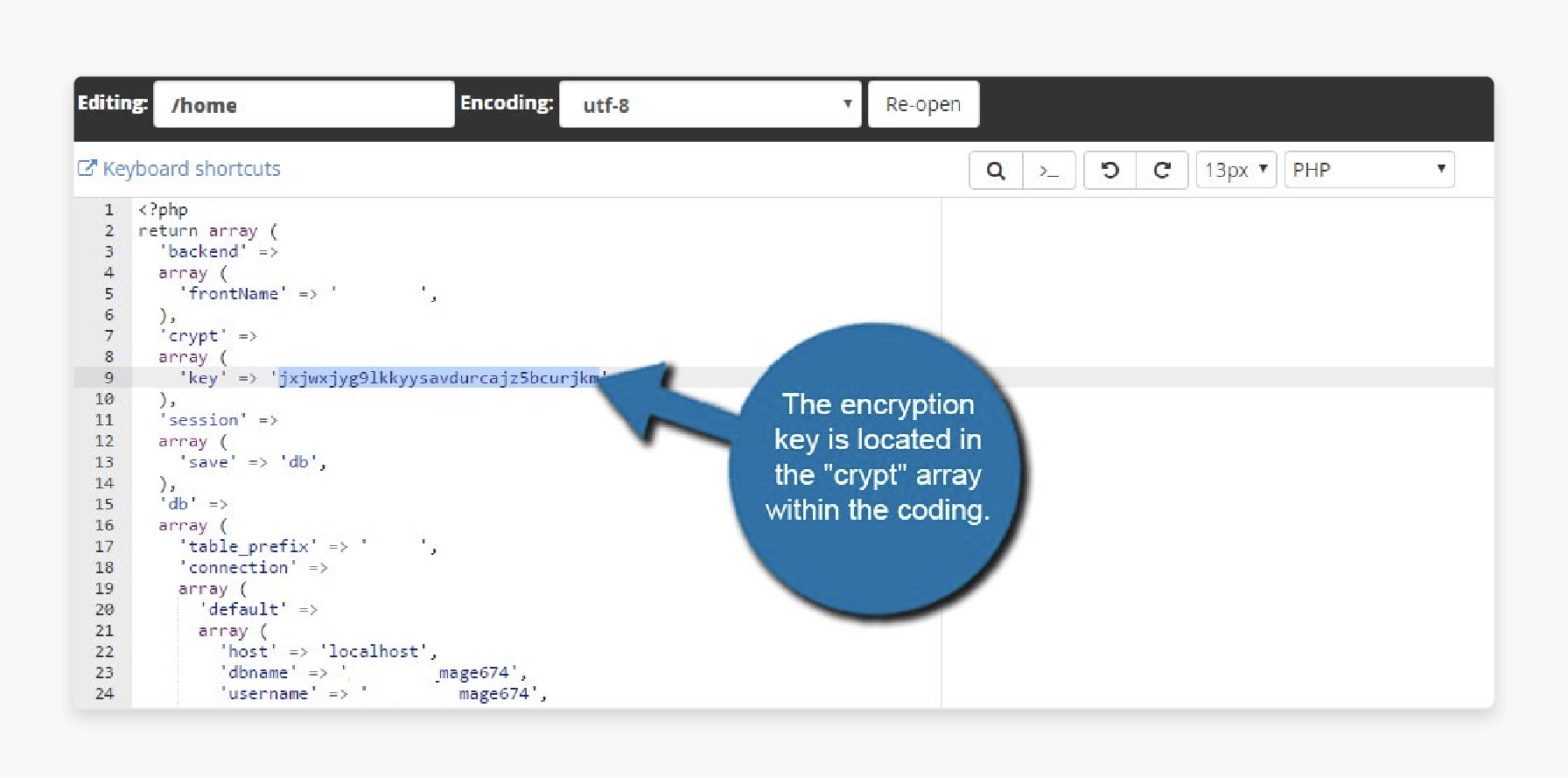
This long string is your security key. Keep it private, and do not share it with anyone. You can also generate a new key if needed, which will make the old one invalid.
Why Encryption Key is Crucial for E-commerce Security?
1. Data Protection
-
Encryption: The key uses strong algorithms like AES-256 to protect private data. It includes credit card numbers and passwords. This makes the data unreadable to anyone who does not have the correct key. Only those with the decoding key can access the information, keeping it secure.
-
Hashing: For non-secure data, the ecommerce platform uses SHA-256 hashing. Hashing changes data into a fixed-size string of characters. This one-way process keeps the data intact because it is nearly impossible to reverse the hash back to the original data.
2. Compliance
-
PCI DSS: The security key is important for meeting PCI DSS requirements. It ensures that businesses follow industry standards. It also protects both the company and its customers from data breaches.
-
Regulatory Compliance: Regularly rotating and managing the key securely is essential. It stays compliant with data protection laws. These practices help keep secure data safe and lower the risk of legal issues.
3. Security Enhancement
-
Key Management: Good key management includes regular key rotation and secure storage. These practices reduce the risk of data breaches and unauthorized access. Businesses should ensure that the encryption key should be changed regularly. It maintains strong security.
-
Secure Transmission: The key ensures that private data is sent securely. It prevents unauthorized access. This is critical for protecting customer information during online transactions.
4. Prevention of Unauthorized Access
-
Access Control: The key limits access to private data. It ensures that only authorized users can uncover it. This is done using role-based access controls (RBAC). It helps keep sensitive information secure.
-
Data Integrity: Maintain the integrity of secure data by preventing unauthorized changes. If someone alters data without the correct key, it becomes corrupted and unusable. It ensures that only valid data is kept.
8 Best Practices of Encryption Key Management
1. Document and Enforce Key Management Policies
Create a centralized key management policy to ensure proper handling of keys. The policy should clearly state who is responsible for each stage of the key lifecycle. It should define access controls, explaining who can use and manage each key. For example, specify when specific keys can and cannot be used. Once the policy is created, enforce it by training your team.
2. Limit Keys to a Single Purpose
Security keys can serve different tasks like encryption, decoding, and protecting other keys. Limit each key to one purpose to make management simpler and enhance security. Using one key for multiple purposes can create vulnerabilities.
3. Do not Hard Code Keys
Avoid embedding keys directly in your program’s source code or configuration files. Hard coding keys raise the risk of exposure if hackers access your source code. It can also make it harder to detect breaches. Instead, store keys separately as environment variables or in secure files. It reduces the risk of exposure and makes it easier to update the encryption key when needed.
4. Consider Hardware Security Modules (HSMs) for Key Storage
Hardware security modules (HSMs) are used for key storage instead of software. They are physical devices designed to store and use security keys securely. Since keys are stored and operated within the HSM, the risk of exposure is lower.
HSMs provide tamper-resistant features and comply with key generation standards. They also improve the speed of encryption and decoding.
5. Use Key Management Systems (KMSs) to Automate Tasks
Key management systems (KMSs) are essential for managing security keys. It helps to secure the keys across different environments. These systems automate key management tasks such as generation, backup, rotation, and destruction. Using a KMS streamlines the process and reduces the risk of human error.
Many organizations use multiple key management solutions to manage their security keys effectively. HSMs often support KMS solutions, and using them together can enhance security. You can automatically generate this key to keep everything running.
6. Conduct Regular Audits
Regular audits of your key management processes help enforce your company’s policies. Audits allow you to limit exposure and reduce the risk of compromised keys. It can lead to data breaches. They also ensure your policies remain effective and up to date. Gather feedback from your team to improve any unclear or outdated guidelines.
7. Create a Disaster Recovery Strategy
Include a disaster recovery strategy in your key management process. Start by identifying potential threats and assessing their impact. Define your key backup strategy, focusing on where to store backups and how often to create them.
Your recovery strategy should include steps to restore and verify keys from backups before using. To test your plan's effectiveness, conduct disaster drills. This helps you find areas that need improvement.
8. Inventory Your Keys and Document Usage
Keeping a complete inventory of your keys is important for audits and disaster recovery. The inventory should include details such as:
-
Key name
-
Description of the key’s purpose
-
Key length, size, and algorithm type
-
Creation, expiration, and rotation dates
-
Storage details and backup locations
-
Authorized users who can access the key
-
The person or department that owns the key
You can also group keys by priority level for recovery situations. It helps your team know where to focus during a disaster. In addition to the inventory, keep access and usage logs up to date. These logs should detail who used the key when they used it, and what information they accessed.
Troubleshooting Security Key Issues in Magento
| Issue | Details |
|---|---|
| Encryption Key Mismatch | The issue occurs when the encryption key in Magento 2.4.6 does not match the key used to encrypt data in the database. If the keys do not match, the system cannot uncover stored data, leading to access errors. It can happen after you update the security key or if different environments are not in sync. |
| Key Rotation Problems | When you change the security keys, previously secure data may become inaccessible. Remember, the encryption key change doesn't re-encrypt existing values automatically. You must follow the instructions on how to change the key to ensure all data remains accessible. |
| Forgotten Encryption Key | Forgetting the security keys creates a big problem because it makes all protected data inaccessible. The keys are essential for decrypting sensitive information. If you retain the old key, recovering the data can be easy, but it may require a complete backup restoration. |
| Errors During Login or Checkout | If there are problems with the security keys, customers may have trouble logging in. They may also face issues with completing purchases on their online store. This can result in error messages or failed transactions. Such problems arise from key mismatches or when the data that needs to be uncovered cannot be accessed. |
| Data Corruption | Data corruption can happen if the encryption key using is mismanaged. The other reason could be if there are issues during migrations or backups. Corruption may lead to unreadable data. It affects the integrity of the information stored in the database. This problem can arise from software bugs, improper key handling, or failure to re-secure data. |
| Third-Party Module Conflicts | Some 3rd party modules may interfere with built-in encryption processes. These conflicts can lead to unexpected behavior. It includes errors when accessing encrypted data or performance optimization issues. Compatibility problems may occur if they use their encryption. It changes how the ecommerce platform manages keys. |
| Permission Issues | File permission issues can stop an ecommerce platform from accessing the env.php file. It is the place where the security keys are stored. If the file is writable, the web server may not have the correct permissions to read or write to it. It can cause errors during the encryption and decoding processes. |
| Security Alerts | Security tools may flag your encryption practices if the keys are weak or not managed well. Weak keys can expose private data to attacks. Alerts about potential issues can indicate for immediate action to improve key management. |
FAQs
1. How do I create a new encryption key in Magento 2?
To create a new security key, go to the Magento 2 admin dashboard. Find the system.xml configuration settings and look for the encryption section. You can then update the encryption key there. Follow the steps outlined in the knowledge base for help.
2. What are the steps to change the encryption key?
To update the Magento security key, first access the admin dashboard. Go to the encryption settings. You can easily change the key and back up the values in the database. Remember, the change doesn't re-secure any config automatically. You will need to perform a re-encryption process after changing the key.
3. How does encryption key rotation work in Magento?
Security key rotation improves security. You can start it via the admin panel by going to the encryption settings. Be sure to follow instructions on how to change your key. It’s important to note the key ID you are replacing to avoid confusion.
4. Where can I find the number of the key in Magento?
You can find the number of the key in the `env.php` file located in the isolated patch of your Magento installation. This file holds your current security keys. Make sure that the file is writable and handle it carefully to prevent unauthorized access.
5. Can I auto-generate a key in Magento 2?
You can auto-generate a key using the admin dashboard. This option simplifies creating secure security keys. Just ensure that the key meets the required length, like 256 bits, for strong security.
6. How does cosmicsting relate to encryption in ecommerce platform?
The term cosmicsting does not directly relate to encryption. However, it is important to handle all encryption-related terms properly. Focus on using correct key management practices to keep data secure. Always check the knowledge base for the latest guidelines on encryption and security.
Summary
Magento 2 encryption key is important for your store’s security. Manage it well to improve security and protect your data. Follow the proper steps to keep your store safe. Consider the following practices:
- Verify Encryption Key: Check that the key is correct and present in all environments.
- Re-secure Personal Data: Use tools or scripts to re-secure secure data.
- Isolated Patches: Apply Adobe patches to fix issues with troubleshooting encryption key rotation.
- Manually Update Encryption Key: Copy and append the keys manually.
- Byte: Always store your keys securely to prevent unauthorized access.
Explore managed Magento services to simplify your encryption key management.









