
AWS Security vs Azure Security: A Comparison for eCommerce Businesses
Deciding between AWS Security vs Azure Security? As eCommerce business owners, online retailers, and web developers continue to explore cloud security, the debate between AWS Security vs Azure Security grows.
Choosing the proper protection for your Magento 2 store is a crucial decision. Which cloud security aligns with your requirements? This article thoroughly compares the features, guiding you toward making an informed decision.
Key Takeaways
- AWS and Azure security feature overview
- Insight into identity and access management (IAM) options
- Analysis of virtual private network (VPN) solutions
- Examination of data encryption methods
- Overview of monitoring tools and threat detection capabilities
- Explore sensitive data discovery and critical management
- Guidance to make an informed decision for your security needs
- Answers to frequently asked questions regarding AWS and Azure security
AWS Security Overview
AWS Security keeps data and apps safe in the cloud using powerful features such as:
- Identity and Access Management (IAM): Controls access to resources
- Virtual Private Cloud (VPC): Creates private networks for added security
- Data Encryption: Protects information from unauthorized access
- Monitoring: Watches for risks and helps maintain a secure environment
Azure Security Overview
Azure Security is essential for cloud users, focusing on high performance and safety with features like:
- Azure AD: Manages access to resources and applications
- Azure Security Center: Offers threat protection and security monitoring
- Hardware Security Modules: Safeguards encryption keys and cryptographic operations
- Key Management: Securely stores and manages cryptographic keys and secrets
AWS Security vs. Azure Security: Cloud Security Comparison
1. Identity and Access Management (IAM)
Amazon Web Service IAM
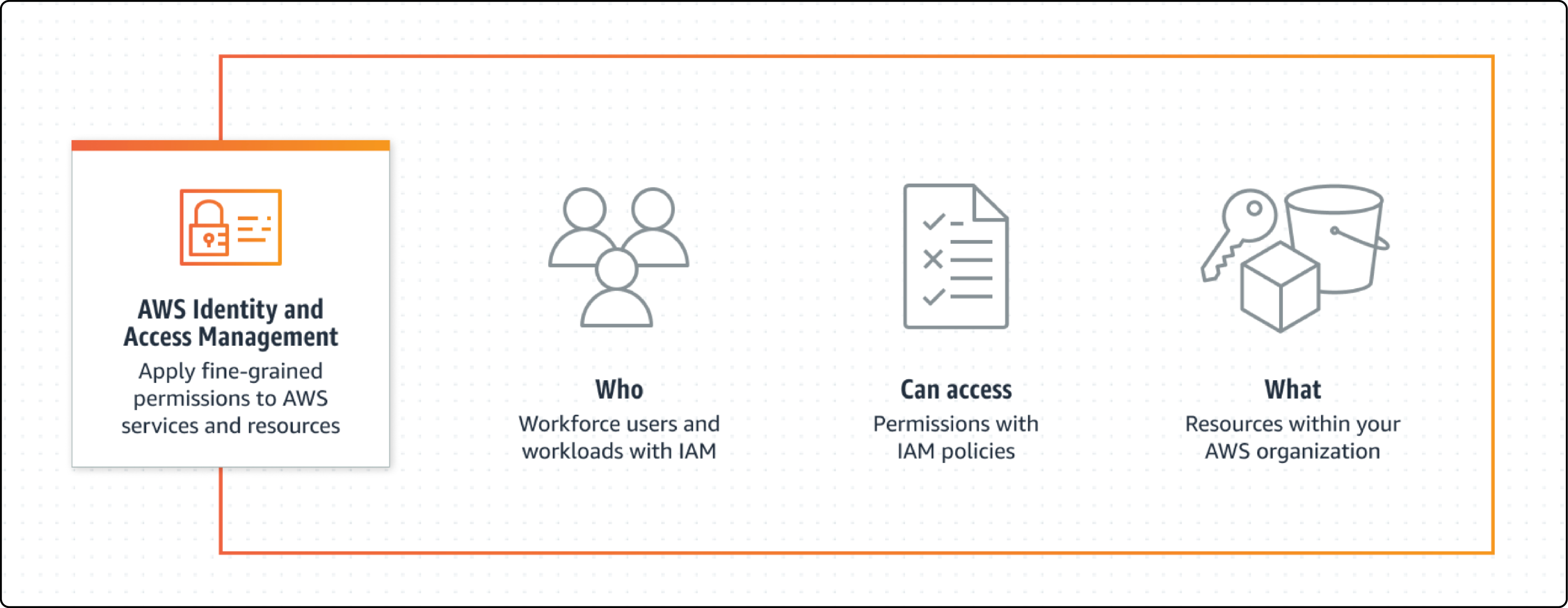
AWS IAM helps control who can access your AWS resources. It allows you to control access to specific resources within the AWS environment.
You can create users, groups, and roles. You can also set permissions and policies for each one. It ensures that only authorized users can access your AWS resources. This helps keep your environment safe and compliant. AWS IAM offers advanced features without extra cost.
Primary features of AWS IAM include:
- Centralized access control for AWS resources
- Fine-grained access control through policies and attribute-based control
- User, group, and role management
- Permissions guardrails
- IAM Access Analyzer for monitoring resource access
- Identity Federation and Single Sign-On
- Multi-factor authentication (MFA)
- PCI DSS compliance
- AWS services integrations and third-party application support
Azure AD (Azure Active Directory)
Azure AD is a cloud-based IAM solution. It helps control who can access resources in the Azure environment. This is part of cloud security best practices. It makes managing users, groups, and apps accessible.
Key features of Azure AD include:
- Cloud authentication
- Unlimited single sign-on (SSO)
- Multi-factor authentication (MFA)
- Role-based access control.
- Integration with on-premises Active Directory

Azure AD requires paid tiers for advanced features like mobile security, reporting, and enhanced monitoring. Azure AD Premium P1 costs $6/user/month, and Premium P2 is $9/user/month. In this comparison, AWS IAM has an advantage as it provides all features for free.
2. Virtual Private Network (VPN)
AWS Virtual Private Cloud (VPC)
A Virtual Private Cloud (VPC) is a safe section of the AWS Cloud. It lets you make a private network for your resources. This keeps them safe from unauthorized access.
In a VPC, you can set your IP address range, create subnets, and set up route tables and network gateways. This lets you control your network and security using AWS and its hybrid environments for scaling and reliability.
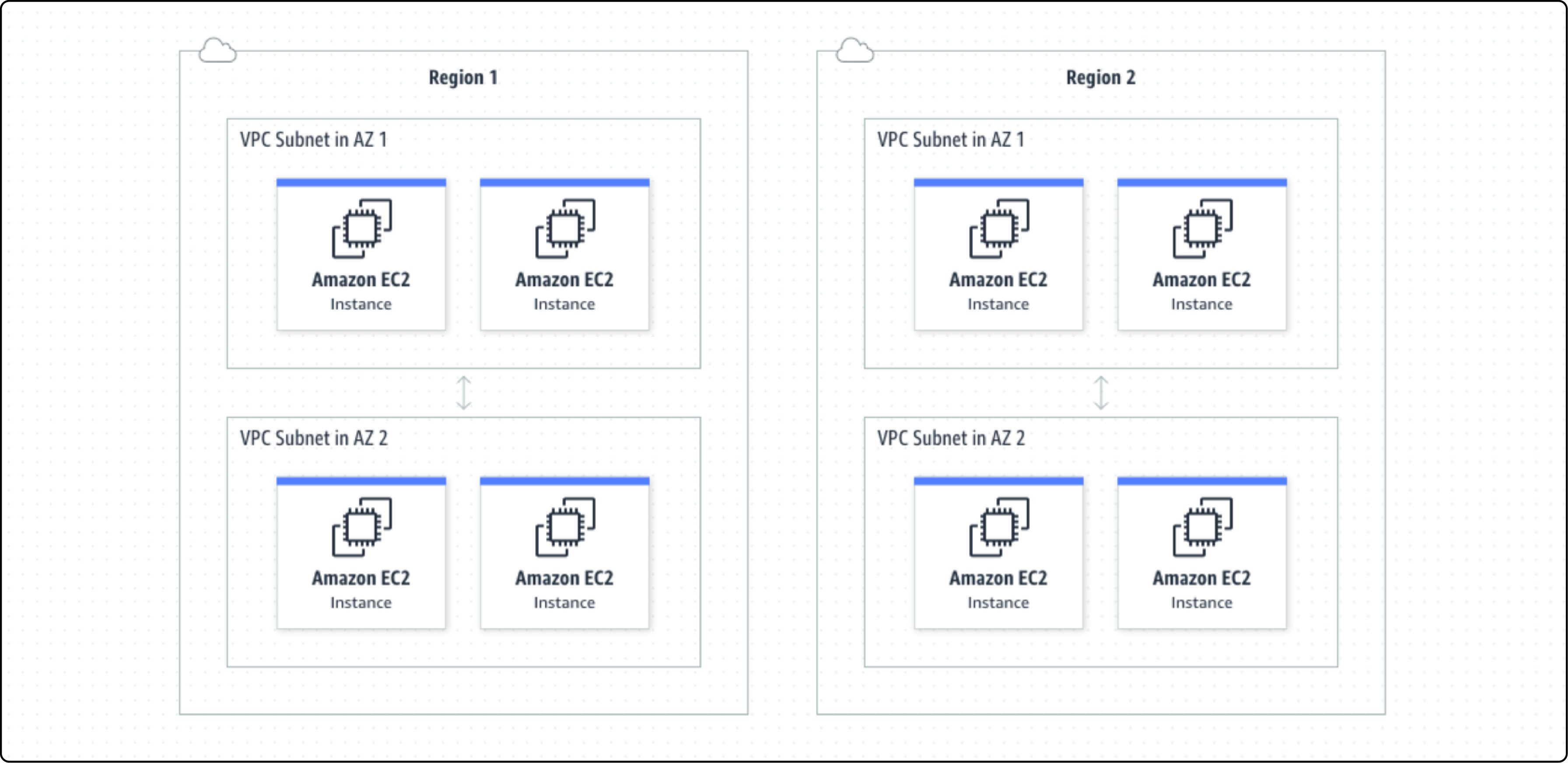
With AWS VPC, you also get the following:
- Access to programmable APIs, CLIs, Cloud Formation Templates
- A management portal for VPC customization
- Multiple architecture options for public and private subnets
- Easy setup for single public subnet or private subnet with hardware VPN access
- The preferred choice for complex, multi-tiered web applications.
Microsoft Azure Virtual Network (VNet)
Azure Virtual Network (VNet) is Microsoft Azure's solution for creating a secure and custom private network in the cloud. It provides high control over network traffic, filtering, and resource communication.
However, unlike AWS VPC, Azure VNet assigns secure internet access to all connected resources by default. It makes it less flexible in terms of public and private network segregation.
Both cloud services offer management tools. It includes portals, command-line interfaces, and automation options to customize your network. AWS VPC is more customer-facing. It is the preferred option for complex networks in multi-tiered web applications. Whereas Azure VNet is more enterprise-focused.
3. Data Encryption
AWS Simple Storage Service (Amazon S3)
Data encryption is essential for protecting your stored data. AWS has many encryption options for data at rest and in transit. You can use AWS Key Management Service or AWS CloudHSM for key management.
You can use AWS Certificate Manager for SSL/TLS certificates for your apps. Storage data encryption helps keep your data secure.
Amazon provides managed critical services through SSE-KMS and SSE-S3 server-side encryption. AWS handles all key managing functions without any intervention from the user’s side.
Azure Blob Storage
Azure Blob Storage, Microsoft's object storage service, provides server-side and client-side encryption using AES-256 symmetric keys. Similar to AWS, Azure offers managed key storage and management.
AWS and Azure have comparable security features. However, AWS has a slight edge due to the inclusion of Galois Counter Mode (GCM) for encryption. AWS also provides more encryption services, key management options, and comprehensive documentation than Azure. Overall, AWS's security offerings are slightly more robust.
4. Monitoring
AWS has tools and services like Amazon CloudWatch, AWS Config, and AWS Trusted Advisor. These allow you to check your resources and find security risks. You can then fix these risks with proper access controls.
AWS CloudWatch
AWS CloudWatch is an essential monitoring tool. It gathers operational and performance data in one place. The dashboard is customizable and focuses on visibility. You can create specific dashboards for distinct application groups.
Visual tools like graphs and metrics offer a quick overview of the AWS infrastructure. CloudWatch uses both user-defined thresholds and machine learning to detect unusual behavior.
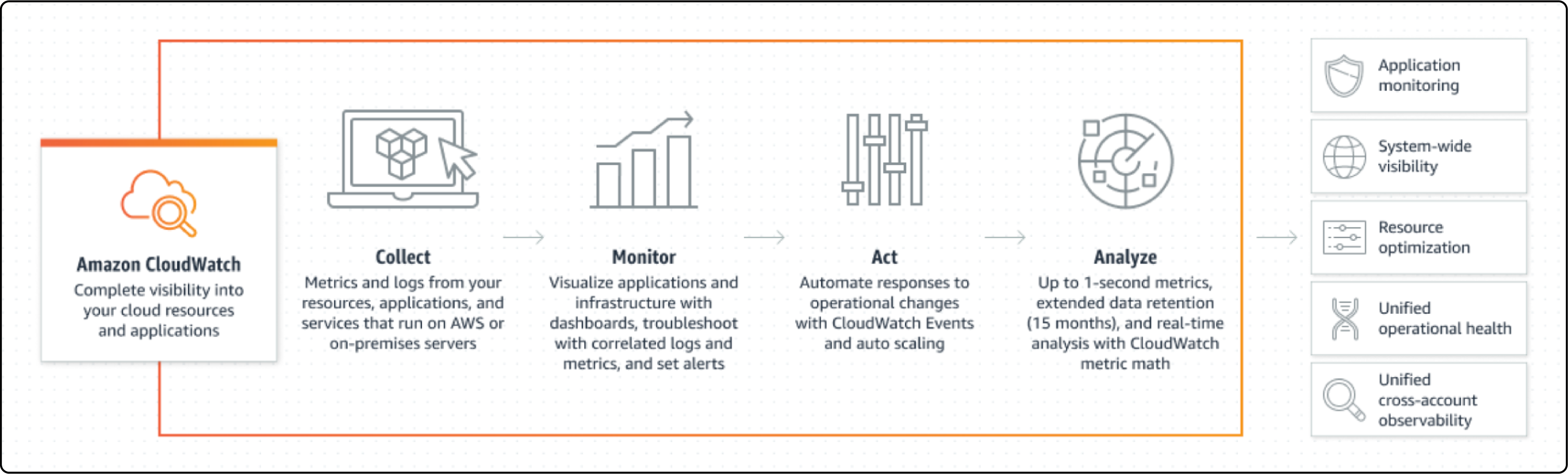
Admins are notified through CloudWatch Alarms. Automated responses can be triggered, like shutting down unused instances.
The platform also automates tasks like capacity and resource planning. It scales performance based on metrics like CPU usage, ensuring efficient management.
Azure Monitor
Azure Monitor collects performance and availability data across Azure, including on-premise and cloud environments. The dashboard may appear more cluttered than CloudWatch, but it simplifies data organization into metrics and logs.
To find relevant data, users must navigate between metrics for issue detection. Azure also provides automation features like auto-scaling resources and security alerts.
Azure depends more on user-defined metrics. AWS CloudWatch uses machine learning for a more intuitive experience. CloudWatch focuses on enhancing incident response and speeding up resolution. This feature is essential for many users of monitoring tools.
5. Threat Detection
AWS Inspector
AWS Inspector is a feature that offers continuous scanning for vulnerabilities in your environment. Some aspects of this service include:
- Agent-based scanning for security
- Limited when compared to Azure's offerings
- Manual remediation required
- Export insights to CSV for analysis
- Vulnerability scanning focused on AWS EC2 instances
With these features, AWS Inspector provides a way to monitor and maintain security, but it requires additional effort for practical use.
Azure Security Center
The Azure Security Center is a security management system. It protects your cloud workloads. It helps you watch your cloud resources and find security risks. Key features of the Azure Security Center include:
- Ongoing security checks and advice for better security
- Threat detection using analytics, machine learning, and intelligence
- Connection with other Azure services for a complete security solution
- Central dashboard for watching and managing security alerts.
Azure provides more robust threat detection through the Azure Security Center. It covers many areas, including firewalls, virtual machines, storage disks, and SQL databases.
Azure Security Center also integrates with Microsoft's Power BI, making report visualization easier. Overall, Azure has slightly better threat detection capabilities compared to AWS.
6. Sensitive Data Discovery
Amazon Macie
Amazon Macie is a valuable data security service in the AWS ecosystem. To utilize Macie, you need to enable it manually.
The service employs machine learning to classify your data and assigns a risk rating to each data type. AWS then uses this information to detect unusual access patterns. It helps to indicate any security breaches.
Key features of Amazon Macie include:
- Monitoring the Amazon S3 security posture
- Machine learning-based data classification
- Detection of unusual access patterns
- Interactive data map for sensitive data in S3
- Custom data type discovery using regular expressions
- Multi-account support with AWS Organizations
In summary, Amazon Macie is crucial in maintaining a secure data environment and ensuring the safety of sensitive information within AWS.
Azure Information Protection
Azure Information Protection (AIP) is part of Microsoft Purview Information Protection. It helps find, classify, protect, and manage sensitive data. AIP enhances Microsoft Purview's labeling features. However, it requires more manual work than Amazon Macie.
Key features of Azure Information Protection include:
- Unified labeling clients for better labeling and protection.
- On-premises scanner to find sensitive content.
- Microsoft Information Protection SDK for third-party app integration.
- File Explorer and PowerShell integration.
- Manual metadata tagging for sensitive data.
While AIP is valid for securing sensitive data in the Azure ecosystem, it needs more manual input. It lacks the automation sophistication of Amazon Macie.
7. Key Management
AWS Key Management
AWS Key Management Service (KMS) employs two encryption key types. It creates a master key for generating data keys, which are used to encrypt and decrypt data.
Users manage their data keys, while master keys can be either customer- or AWS-managed. AWS KMS relies on FIPS 140-2 hardware security modules.
Features of AWS KMS include:
- Centralized key management for simplified control.
- Integration with other AWS services for seamless encryption.
- Automatic key rotation for enhanced security.
- Secure key storage with hardware security modules.
- Compliance with various security standards and regulations.
Using AWS KMS, users can ensure high security and manageability for their encryption keys within the AWS ecosystem.
Azure Key Management
Azure Key Vault is a service for managing and storing keys, secrets, and certificates. It contains the whole life of keys. Key features of Azure Key Vault include:
- Safe storage of keys and secrets using 140-2 Level 2 approved hardware
- Access control and audit logging for watching critical use
- Connection with Azure services for easy encryption and decryption
- Support for HSMs for better essential protection
Using Azure Security features helps keep your data and apps safe in the cloud. This also enables you to follow the rules and standards.
8. Hardware Security Modules
AWS CloudHSM
AWS CloudHSM offers hardware security modules (HSMs) within the AWS Cloud. HSMs are devices that handle cryptographic operations. With AWS CloudHSM, you can perform various tasks:
- Create, store, import, export, and manage cryptographic keys.
- Encrypt and decrypt data using symmetric and asymmetric algorithms.
- Sign data cryptographically (including code signing) and verify signatures.
- Generate cryptographically secure random data.
Azure HSM
Azure has hardware security modules for protecting keys and cryptographic operations. HSMs keep keys safe in a secure environment. Key features of Azure HSMs include:
- FIPS 140-2 Level 3 approved hardware.
- Support for many cryptographic algorithms. It includes RSA, ECDSA, and AES
- Connection with Azure Key Vault for secure key storage
FAQ: AWS Security vs Azure Security
1. Which is more secure, Azure or AWS?
AWS and Azure are both secure cloud platforms, offering encrypted data, threat protection, and secure data centers. However, AWS holds a slight edge with more robust security features. Both platforms have a free tier with security services, so compare their features and choose based on your needs.
2. Does Azure have security groups like AWS?
Yes, Azure has Network Security Groups that function like AWS Security Groups. They allow you to control inbound and outbound network traffic to resources in your cloud environment.
3. Is AWS good for security?
Yes, AWS offers robust security features, including encryption, compliance certifications, and various security services. It is a trusted cloud platform for many businesses due to its strong security measures.
4. How do AWS and Azure security features affect cost and pricing?
AWS and Azure have different pricing models, which can impact the overall cost of implementing their security features.
AWS often provides more security features at no additional cost. Azure may require paid tiers for certain advanced features. Evaluate the cost-effectiveness of each platform's security offerings for your business.
Summary
In this article, we explored AWS Security vs Azure Security. We compared identity management, VPNs, encryption, monitoring, and threat detection features. AWS emerged as the recommended option with better cloud security offerings.
Stay updated with Magento news and make well-informed decisions for your eCommerce business.








